Hyper-V Best Practices – Optimize Your Virtualization Setup
Virtualization has become an essential component of modern IT infrastructure, enabling organizations to optimize their resources, improve efficiency, and reduce costs. Microsoft Hyper-V, a popular virtualization technology, allows for the creation and management of virtual machines (VMs) on a physical server. It enables multiple operating systems to run simultaneously on the same hardware, providing both flexibility and scalability. In this comprehensive guide, we will explore Hyper-V best practices that will help you get the most out of your virtual environment, ensuring optimal performance, security, and manageability. We will discuss various aspects of Hyper-V, including understanding its architecture, setting it up, configuring hosts, managing storage, optimizing virtual machines, enhancing security, monitoring performance, and more.
Understanding Hyper-V
What is Hyper-V?
Microsoft Hyper-V is a virtualization technology that enables the creation and management of virtual machines on a physical server. It allows multiple operating systems to run simultaneously on the same hardware, providing several benefits, such as cost reduction, increased efficiency, improved flexibility, and simplified management. By leveraging Hyper-V, organizations can consolidate their workloads, reduce their physical server footprint, and improve resource utilization.
Hyper-V Versions
Hyper-V has evolved through several versions since its initial release with Windows Server 2008. Each subsequent version has introduced enhancements and improvements in performance, security, and scalability. The most recent version, Hyper-V on Windows Server 2022, offers several new features and capabilities, such as improved virtual hardware, enhanced virtual network support, and more efficient storage management. Organizations should stay up-to-date with the latest Hyper-V releases to take advantage of new features and improvements
Hyper-V Architecture
The Hyper-V architecture is a critical aspect of understanding how the technology works and how to optimize it for maximum performance and efficiency. The architecture consists of three main components: the parent partition, child partitions, and the virtualization stack.
Parent Partition
The parent partition is the primary partition on a Hyper-V host, which runs the Hyper-V hypervisor. It is responsible for managing child partitions and providing them with access to the physical hardware resources. The parent partition has direct access to the hardware and runs the management operating system, typically Windows Server. Administrators interact with the parent partition to configure and manage the virtual environment, create and manage virtual machines, and perform other administrative tasks.
Child Partitions
Child partitions are isolated environments where virtual machines run. Each virtual machine operates within its child partition, which has virtualized access to hardware resources such as CPU, memory, and storage. The child partitions are created and managed by the parent partition, ensuring isolation and resource allocation for each virtual machine.
Virtualization Stack
The virtualization stack is a critical component of the Hyper-V architecture that manages and allocates hardware resources to virtual machines. It is responsible for ensuring that VMs can access hardware resources efficiently and securely. The virtualization stack includes the hypervisor, virtual machine manager, and other components that work together to provide a seamless and efficient virtual environment.
Setting up Hyper-V
Hardware Requirements
Before setting up Hyper-V, it’s essential to ensure that your hardware meets the minimum requirements for running the technology. To run Hyper-V, you need a 64-bit processor with hardware-assisted virtualization and Second Level Address Translation (SLAT). Additionally, you should ensure that virtualization support is enabled in the BIOS of your server. Other factors to consider include the amount of memory and storage capacity required for your virtual environment, as well as the need for high-performance networking components.
Installation Process
Installing Hyper-V involves adding the Hyper-V role to a Windows Server operating system. This can be done through the Server Manager or using PowerShell commands. The installation process requires a server restart, after which you can begin creating and managing virtual machines. It’s essential to follow best practices during the installation process, such as ensuring that the latest updates and patches are applied to the server and that proper hardware and software configurations are in place.
Hyper-V Best Practices
Optimizing your Hyper-V environment requires attention to various aspects, such as host configuration, storage management, virtual machine optimization, and security. In this section, we will explore these areas in detail, providing recommendations for best practices that will help you achieve the best possible performance, security, and manageability.
Host Configuration
Hardware Selection
Choosing the right hardware for your Hyper-V host is a crucial aspect of ensuring optimal performance and reliability. Factors to consider when selecting hardware include the processor, memory, storage capacity, and networking components. Investing in high-quality, enterprise-grade hardware components will provide a more stable and reliable virtual environment.
When selecting a processor, consider the number of cores and threads, as well as the clock speed, to ensure sufficient processing power for your virtual machines. Additionally, ensure that the processor supports hardware-assisted virtualization and SLAT.
Memory is another critical factor, as it directly impacts the performance of your virtual machines. Ensure that your server has enough memory to support the number of virtual machines you plan to run, as well as any additional memory requirements for the host operating system and other software components.
Network Configuration
Properly configuring your Hyper-V host’s network settings is essential for improving performance and reducing latency. Key aspects of network configuration include setting up virtual switches, configuring virtual network adapters, and using dedicated network adapters for management and live migration.
Setting up virtual switches involves creating a virtual switch for each physical network adapter on the host. This allows virtual machines to connect to the physical network and communicate with other devices. When configuring virtual network adapters, ensure that they are connected to the appropriate virtual switch and configured with the correct network settings.
Using dedicated network adapters for management and live migration can help to improve performance by isolating these tasks from other network traffic. For instance, you can dedicate one network adapter for host management, another for live migration, and a third for virtual machine communication.
Storage
Storage Types
Selecting the appropriate storage type for your Hyper-V environment is crucial for achieving optimal performance and reliability. There are several storage options available, including local storage, network-attached storage (NAS), and storage area network (SAN). Each storage type has its advantages and disadvantages, so it’s essential to evaluate your needs and budget when making a decision.
Local storage is the simplest and most affordable option, as it involves using the server’s internal storage for virtual machine files. However, it may not offer the best performance or scalability, especially for larger virtual environments.
Network-attached storage (NAS) is a more scalable option, allowing you to connect multiple servers to a centralized storage device over the network. NAS devices typically offer better performance and reliability than local storage but can be more expensive and complex to set up and manage.
Storage area networks (SAN) provide the highest performance and scalability, as they allow for direct, high-speed connections between servers and storage devices. However, SANs can be the most expensive and complex storage option, requiring specialized hardware and expertise to manage effectively.
Storage Configuration
Optimizing your storage configuration is essential for improving performance and ensuring data redundancy. Some best practices for storage configuration include using RAID arrays for fault tolerance, separating storage workloads, and using storage tiering to optimize performance.
RAID arrays can help protect your data in the event of a disk failure, ensuring that your virtual environment remains operational. There are various RAID levels available, each offering different levels of performance and redundancy. Choose the RAID level that best suits your needs and budget.
Separating storage workloads can help improve performance by reducing contention for storage resources. For example, you can store virtual machine configuration files, virtual hard disks, and snapshots on separate storage devices or arrays to minimize the impact of storage-related tasks on the overall performance of your environment.
Storage tiering is another way to optimize performance, as it involves grouping storage devices based on their performance characteristics and automatically moving frequently accessed data to faster storage tiers. This can help to ensure that your most critical data is stored on the fastest available storage, while less frequently accessed data is stored on slower, more cost-effective storage devices.
Virtual Machines
VM Configuration
Properly configuring your virtual machines is essential for optimizing performance and resource utilization. This includes setting the right amount of virtual processors, memory, and storage. Avoid over-provisioning resources to prevent performance issues and ensure that resources are allocated efficiently across all virtual machines.
When configuring virtual processors, it’s important to consider the number of physical processor cores and threads available on the host, as well as the processing requirements of your virtual machines. Over-provisioning virtual processors can lead to performance issues, as it can cause contention for processing resources.
Similarly, when configuring virtual machine memory, ensure that you allocate enough memory for the guest operating system and applications to run smoothly, without over-allocating memory resources. Over-provisioning memory can lead to unnecessary resource contention and reduced performance.
Generation Selection
Choose the appropriate generation for your virtual machines based on their requirements. Generation 1 virtual machines offer legacy support for older operating systems, while Generation 2 virtual machines provide improved performance and support for newer features. To learn more about the differences between Gen 1 and Gen 2 virtual machines, you can refer to this comprehensive guide.
Security
Shielded VMs
Implement Shielded virtual machines to protect sensitive data and ensure the integrity of your virtual machines. Shielded VMs use encryption and secure boot features to protect against unauthorized access and tampering. By leveraging Shielded VMs, you can safeguard your virtual environment from potential security threats and maintain compliance with industry regulations.
Regular Patching and Updates
Ensure that your Hyper-V host, guest operating systems, and applications are regularly patched and updated to protect against security vulnerabilities. This includes applying security updates, hotfixes, and service packs to your host and guest operating systems, as well as updating any third-party applications running within your virtual environment.
Monitoring and Management
Proactive Monitoring
To ensure the stability and reliability of your Hyper-V environment, implement proactive monitoring of your host servers, virtual machines, storage, and network resources. Monitoring tools and services can help you identify potential issues before they escalate into more significant problems, allowing you to take corrective action promptly.
Monitoring should include tracking CPU, memory, and storage usage, as well as network traffic and latency. By setting up alerts and notifications for specific events or thresholds, you can receive timely information about the health and performance of your virtual environment.
Centralized Management
Utilize centralized management tools and solutions to simplify the administration of your Hyper-V environment. Centralized management allows you to manage and monitor multiple Hyper-V hosts and virtual machines from a single interface, reducing the complexity of managing your virtual infrastructure.
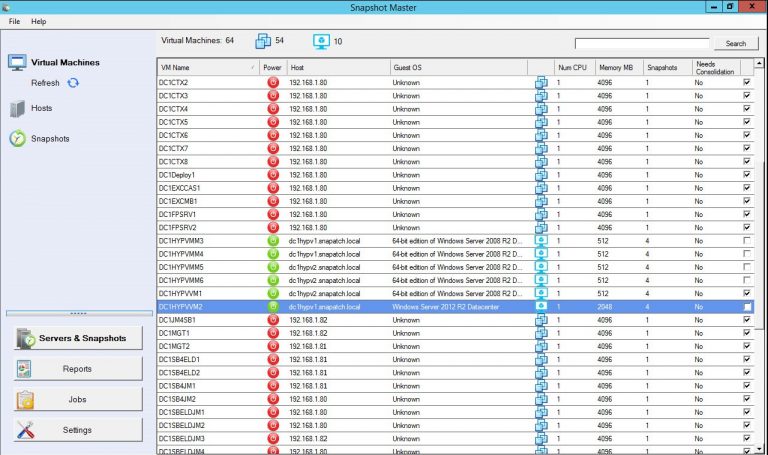
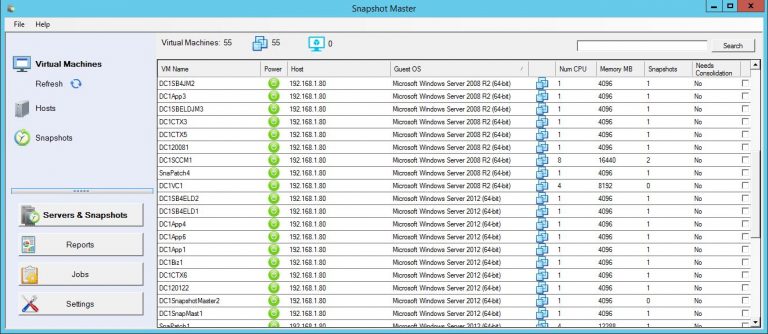
Tools like System Center Virtual Machine Manager (SCVMM) and SnapShot Master can help you manage and automate various tasks, such as creating, configuring, and deleting virtual machines, managing storage, and configuring networking. By leveraging centralized management tools, you can improve efficiency and reduce the potential for errors in your virtual environment.
Backup and Disaster Recovery
Implementing a robust backup and disaster recovery strategy is essential for protecting your virtual environment and ensuring business continuity in the event of a disaster or data loss. Regularly backing up your Hyper-V host, virtual machines, and their associated data will enable you to recover your environment quickly and with minimal downtime.
When developing a backup strategy, consider the use of incremental backups, which only capture changes made since the last backup, to reduce storage requirements and improve backup performance. Additionally, test your backups regularly to ensure that they can be restored successfully in the event of an emergency.
For disaster recovery, consider using replication and failover technologies to create redundant copies of your virtual machines and data, allowing you to quickly recover your environment in the event of a disaster. Hyper-V Replica is a built-in feature that enables you to replicate virtual machines between Hyper-V hosts, while other third-party solutions are also available for more advanced disaster recovery capabilities.
Optimizing Hyper-V Networking
Virtual Machine Queue (VMQ)
To optimize network performance for your virtual machines, enable Virtual Machine Queue (VMQ) on your Hyper-V host’s network adapters. VMQ is a feature that offloads the processing of network traffic from the host’s processor to the network adapter, reducing the CPU overhead and improving network throughput.
To enable VMQ, ensure that your network adapters support this feature and that it is enabled in the adapter’s settings. Additionally, configure the number of processor cores and memory resources allocated to VMQ based on your host’s hardware and network requirements.
Receive Side Scaling (RSS)
Receive Side Scaling (RSS) is another feature that can help improve network performance in your Hyper-V environment. RSS enables the network adapter to distribute incoming network traffic across multiple processor cores, reducing the CPU overhead and improving overall network throughput.
To enable RSS, ensure that your network adapters support this feature and that it is enabled in the adapter’s settings. Additionally, configure the number of processor cores and memory resources allocated to RSS based on your host’s hardware and network requirements.
Hyper-V Conclusion
Following Hyper-V best practices is essential for optimizing the performance, security, and manageability of your virtual environment. By paying close attention to host configuration, storage management, virtual machine optimization, and security, you can ensure that your Hyper-V environment is operating at its full potential. As virtualization technology continues to evolve, staying up-to-date with the latest best practices and advancements in Hyper-V will help you maintain a reliable, high-performing, and secure virtual environment.
Frequently Asked Questions (FAQs)
What is the difference between Generation 1 and Generation 2 virtual machines in Hyper-V?
Generation 1 virtual machines offer legacy support for older operating systems, while Generation 2 virtual machines provide improved performance and support for newer features, such as UEFI firmware, secure boot, and larger virtual disk capacities.
Can I mix different storage types in my Hyper-V environment?
Yes, you can use a combination of local storage, NAS, and SAN storage in your Hyper-V environment, depending on your needs and budget. Each storage type has its advantages and disadvantages, so it’s essential to evaluate your requirements carefully when selecting storage solutions.
What are the hardware requirements for running Hyper-V?
To run Hyper-V, you need a 64-bit processor with hardware-assisted virtualization and Second Level Address Translation (SLAT) support. Additionally, you should ensure that virtualization support is enabled in the BIOS of your server. Other factors to consider include the amount of memory and storage capacity required for your virtual environment, as well as the need for high-performance networking components.
How can I improve the performance of my virtual machines in Hyper-V?
To improve the performance of your virtual machines, ensure that you allocate the appropriate amount of virtual processors, memory, and storage. Avoid over-provisioning resources to prevent performance issues and ensure that resources are allocated efficiently across all virtual machines. Additionally, follow best practices for storage configuration, such as using RAID arrays for fault tolerance, separating storage workloads, and implementing storage tiering.
-
What are Shielded VMs, and why should I use them?
Shielded virtual machines are a security feature in Hyper-V that protects sensitive data and ensures the integrity of your virtual machines. They use encryption and secure boot features to protect against unauthorized access and tampering. By implementing Shielded VMs, you can safeguard your virtual environment from potential security threats and maintain compliance with industry regulations.