How to upgrade SCCM 1610

Microsoft has recently released SCCM 1610, the much-awaited upgrade to their System Center Configuration Manager. This upgrade includes new features and enhancements in Office 365 management, application management, Windows 10, client management, end-user experience, and new functionality for customers using Intune with SCCM. In this article, we will discuss how to upgrade to SCCM 1610 and its new features and enhancements.
A quick overview of these enhancements are;
- Windows 10 Upgrade Analytics integration allows you to assess and analyze device readiness and compatibility with Windows 10 to allow smoother upgrades.
- Office 365 Servicing Dashboard and app deployment to clients features help you to deploy Office 365 apps to clients as well as track Office 365 usage and update deployments.
- Software Updates Compliance Dashboard allows you to view the current compliance status of devices in your organization and quickly analyze the data to see which devices are at risk.
- Cloud Management Gateway provides a simpler way to manage Configuration Manager clients on the Internet. You can use the ConfigMgr console to deploy the service in Microsoft Azure and configure the supported roles to allow cloud management gateway traffic.
- Client Peer Cache is a new built-in solution in Configuration Manager that allows clients to share content with other clients directly from their local cache with monitoring and troubleshooting capabilities.
- Enhancements in Software Center including customizable branding in more dialogs, notifications of new software, improvements to the notification experience for high-impact task sequence deployments, and ability for users to request applications and view request history directly in Software Center.
- New remote control features including performance optimization for remote control sessions and keyboard translation.
and if you use SCCM with Microsoft’s Intune you get the following new features;
- New configuration item settings and improvements now only show settings that apply to the selected platform. We also added lots of new settings for Android (23), iOS (4), Mac (4), Windows 10 desktop and mobile (37), Windows 10 Team (7), Windows 8.1 (11), and Windows Phone 8.1 (3).
- Lookout integration allows to check device’s compliance status based on its compliance with Lookout rules.
- Request a sync from the admin console improvement allows you to request a policy sync on an enrolled mobile device from the Configuration Manager console.
- Support for paid apps in Windows Store for Business allows you to add and deploy online-licensed paid apps in addition to the free apps in Windows Store for Business.
SCCM 1610 FAQs
| Question |
Answer |
What is SCCM 1610?
|
SCCM 1610 is the upgrade to Microsoft’s System Centre Configuration Manager. |
What new features are included in SCCM 1610?
|
SCCM 1610 includes new features and enhancements in Office 365 management, Windows 10, application management, client management, end user experience, and new functionality for customers using Intune with SCCM. |
What is Windows 10 Upgrade Analytics integration?
|
Windows 10 Upgrade Analytics integration allows you to assess and analyze device readiness and compatibility with Windows 10 to allow smoother upgrades. |
What is the Office 365 Servicing Dashboard?
|
The Office 365 Servicing Dashboard is a feature that helps you to deploy Office 365 apps to clients as well as track Office 365 usage and update deployments. |
What is the Software Updates Compliance Dashboard?
|
The Software Updates Compliance Dashboard allows you to view the current compliance status of devices in your organization and quickly analyze the data to see which devices are at risk. |
What is the Cloud Management Gateway?
|
The Cloud Management Gateway provides a simpler way to manage Configuration Manager clients on the Internet. You can use the ConfigMgr console to deploy the service in Microsoft Azure and configure the supported roles to allow cloud management gateway traffic. |
What is Client Peer Cache?
|
Client Peer Cache is a new built-in solution in Configuration Manager that allows clients to share content with other clients directly from their local cache with monitoring and troubleshooting capabilities. |
What are the enhancements in Software Center?
|
The enhancements in Software Center include customizable branding in more dialogs, notifications of new software, improvements to the notification experience for high-impact task sequence deployments, and ability for users to request applications and view request history directly in Software Center. |
What are the new remote control features?
|
The new remote control features include performance optimization for remote control sessions and keyboard translation. |
What new features are available if you use SCCM with Microsoft’s Intune?
|
If you use SCCM with Microsoft’s Intune, you get new configuration item settings and improvements, Lookout integration, Request a sync from the admin console improvement, and support for paid apps in Windows Store for Business. |
How do you upgrade to SCCM 1610?
|
To upgrade to SCCM 1610, you need to follow several steps, including checking to see if SCCM 1610 has downloaded, enabling the Fast Ring, forcing a check for the update, and downloading and installing the SCCM 1610 update. |
Upgrade to SCCM 1610
Now to upgrade your SCCM to version 1610, follow the following steps;
Check to see if SCCM 1610 has downloaded.
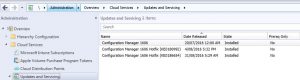
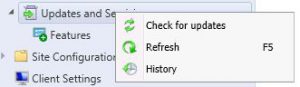
Open your SCCM console, and go to Administration, expand Cloud Services, then Updates and Servicing.

As in the picture above, you can see that the update to SCCM 1610 has not downloaded as yet. You can choose to right click and check for updates, but as Microsoft are slowly rolling out this update over the next few weeks it may not download. If you cannot wait for it to download itself, you can force the update to do so by running the following Powershell script located here https://gallery.technet.microsoft.com/ConfigMgr-1610-Enable-046cc0e9
Download SCCM 1610 Fast Ring
If you have waited quite sometime and SCCM 1610 hasn’t downloaded, then you need to download the EnableFastRing.Exe to do this for you. Once downloaded. launch the file and extract the powershell script and follow these steps.

- Launch an elevated command prompt
- Run PowerShell
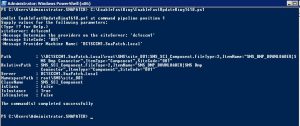
- Run the EnableFastUpdateRing1610.ps1 script
- EnableFastUpdateRing1610.ps1 where SiteServer refers to the CAS or standalone primary site server
- Force a check for the update.
- If you are upgrading from version 1602 or higher go to Administration, Overview, Cloud Services, Updates and Servicing and click “Check for Updates”. You may need to try “Check for Updates” more than once if the package is not downloaded on the first try.
- If you are upgrading from version 1511, restart the SMS_Executive.
- The new 1610 Update should now be available in the Configuration Manager Console.
Download SCCM 1610 update
Now that Fastring has been enabled, go back to your SCCM console and right click the Updates and Servicing node and click check for updates.

Give SCCM sometime to start the download of SCCM 1610. Refresh the console to see the status and then proceed to install when downloaded.

SCCM 1610 Downloaded
Now hopefully your SCCM 1610 update has downloaded and is now available in your console.

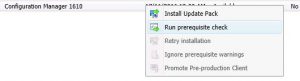
Select the Configuration Manager 1610 update, right click and choose Run prerequisite check.

SCCM will now check your environment is ready for the upgrade to SCCM 1610.

Let SCCM complete the check, refresh the console to see when it has completed.

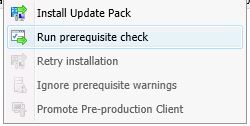
SCCM 1610 Update Installation
Now that the prerequisites have been checked and passed, you can now start to install the upgrade to SCCM 1610. Right click the update and choose Install Update Pack.

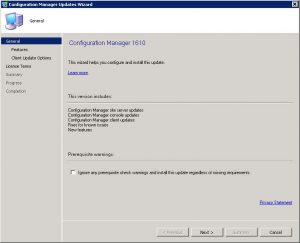
SCCM 1610 Update Installation – General Tab
The General Tab starts off the installation of the SCCM 1610 update. Click Next when you are ready to install.

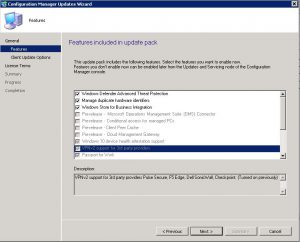
SCCM 1610 Update Installation – Features Tab
On the Features tab, you can select which options you wish to install. Click Next when ready to proceed.

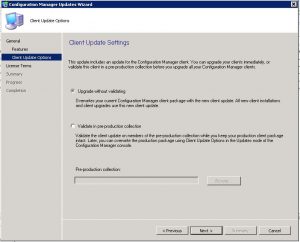
SCCM 1610 Update Installation – Client Update Options Tab
Next is the Client update options Tab, you can choose on this tab to upgrade without validating or validate the upgrade in a pre-production collection. As this is one of our lab environments, I have chosen to upgrade without validating. If this is your production environment, it always pays to be mindful of any upgrades, SCCM included so it may be worth you choosing the other option and validating the upgrade against a test collection.
Choose the option you wish and click Next.

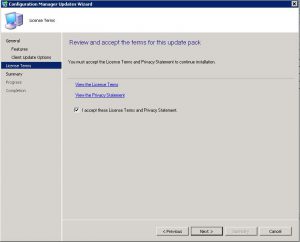
SCCM 1610 Update Installation – Licensing Terms Tab
Accept the license terms and privacy statement and click Next.

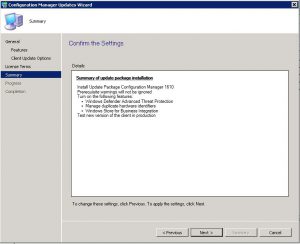
SCCM 1610 Update Installation – Summary Tab
On the Summary Tab, confirm the options you have chosen are correct and then click on Next to continue.

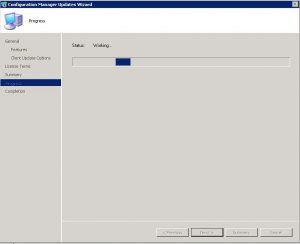
SCCM 1610 Update Installation – Progress Tab
The update to SCCM 1610 will now install.

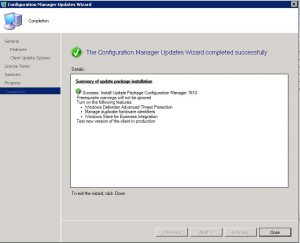
SCCM 1610 Update Installation – Completion Tab
Hopefully all went with your installation of SCCM 1610 and you should see a screen similar to the one below. Click now on Close and SCCM will continue updating in the background.

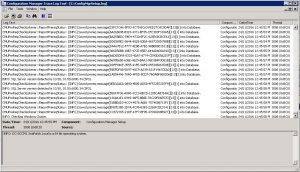
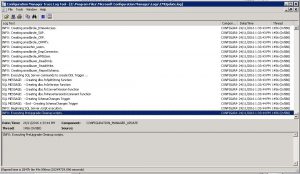
SCCM 1610 Update Installation – Update Log
To view the installation logs, go to your C Drive of your SCCM server and locate the ConfigMgrSetup.log. If you have Trace32 installed, double click the log file to see the installation status.

Refreshing the console shows that the SCCM 1610 update is installing. Depending on your infrastructure, this could take some time.

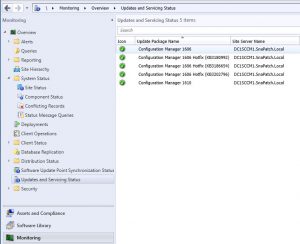
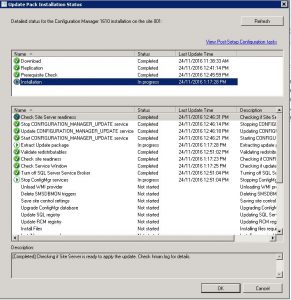
Monitor the SCCM 1610 upgrade – Installation Status
You can additionally monitor the status of the installation of SCCM 1610 in your console. Go to the Monitoring tab, then Updates and Servicing Status where you can see the updates you have applied. Highlight the Configuration Manager 1610 update and right click and chose show status.


Also, the cmupdate.log contains more details of the installation progress.

You should see after quite sometime that your SCCM version is now showing as version SCCM 1610

You can finally go and party like its 1999. Dont forget since you are here, to check out our many software products that help make an Administrators life easy.