by Mark | Mar 16, 2023 | Patch Management, Patch Releases
In today’s digital world, software vulnerabilities have become a widespread concern. Cybercriminals are always looking for ways to exploit these vulnerabilities, resulting in devastating security breaches. That’s where patch management comes in. In this article, we’ll discuss what patch management is, its importance, and best practices to implement it.
What is Patch Management?
Patch management is the process of acquiring, testing, and installing software updates or patches to address vulnerabilities or issues in software applications. Software developers regularly release patches to fix software vulnerabilities or bugs that have been discovered.
Patch management is a critical aspect of cybersecurity. Cybercriminals often use unpatched software vulnerabilities as a way to infiltrate computer systems, networks, or applications. As a result, the implementation of patch management is necessary to ensure the security and integrity of computer systems and networks.
Why is Patch Management Important?
Patch management is essential because it helps to ensure that software applications are up to date and secure. Cybersecurity is an ongoing process that requires constant attention and maintenance. Failing to implement patch management leaves systems vulnerable to security breaches, which could have disastrous consequences.
The Risks of Not Implementing Patch Management
Failing to implement patch management can lead to several risks. Some of these risks include:
- Cyber attacks: Unpatched vulnerabilities provide an open door for cybercriminals to exploit computer systems or networks.
- Data breaches: Cybercriminals use unpatched vulnerabilities to gain unauthorized access to sensitive data or personally identifiable information.
- Legal consequences: Non-compliance with data protection laws can result in legal action or fines.
- Reputation damage: Cybersecurity breaches can have a significant impact on an organization’s reputation.
Best Practices for Patch Management
Patch management can be a complex process, but some best practices can help make the process more manageable. These include:
- Developing a patch management policy
- Prioritizing patches based on criticality
- Regularly testing patches before deployment
- Automating patch management where possible
- Establishing a patch management team
- Maintaining an inventory of hardware and software
The Patch Management Process
The patch management process typically involves four steps:
- Discovery: Identifying the software applications that require updates or patches.
- Assessment: Determining the criticality of the vulnerabilities and prioritizing patches.
- Testing: Testing patches to ensure they do not cause any adverse effects on software applications or systems.
- Deployment: Installing patches and monitoring their effectiveness.
The Importance of Testing Patches
Testing patches is critical to the patch management process. It ensures that patches do not cause any adverse effects on software applications or systems. Testing should be conducted in a controlled environment to minimize the risk of any issues occurring.
Automating Patch Management
Automating patch management can make the process more efficient and reduce the workload on IT staff. Automated patch management systems can detect and deploy patches automatically, reducing the risk of human error and ensuring that software applications are up to date.
Developing a Patch Management Policy
Developing a patch management policy is an essential component of patch management. The policy should outline the process for acquiring, testing, and installing patches. It should also specify who is responsible for each step of the process and what actions will be taken in the event of a security breach.
The Role of Cybersecurity Professionals in Patch Management
Cybersecurity professionals play a crucial role in patch management. They are responsible for identifying vulnerabilities, testing patches, and ensuring that patches are deployed promptly. Cybersecurity professionals should also monitor systems and applications for any signs of unauthorized access or security breaches.
SnaPatch: Streamline Your Patch Management with SCCM Add-On
SnaPatch is a patch management add-on for System Centre Configuration Manager (SCCM) that automates the snapshot process of virtual machines before deploying Windows patches. With SnaPatch, you can easily and quickly schedule snapshots of your virtual machines, which allows you to restore to the original state if any patch causes an issue to your virtual machines.
This tool also integrates with Microsoft’s SCCM and VMware or HyperV, giving you access to view detailed information about your SCCM environment. You can see the patching compliance of each server from within each collection, with detailed information about the number of updates missing for each class (i.e., security, critical, service packs, etc.).
Moreover, SnaPatch lets you deploy patches directly to your SCCM clients from the tool, and it automatically deletes snapshots based on retention policy. With email reminders before the system deletes them, you can exclude servers from the snapshot auto-delete policy.
If you are looking for a patch management solution for your SCCM, SnaPatch is the right tool for you. It is easy to set up, with a simple and intuitive interface. You can be up and running in less than 30 minutes. Try SnaPatch today, and you will have a reliable, fast roll-back solution that helps you avoid the inherent risk of patching and updating servers.
Conclusion
Patch management is a critical aspect of cybersecurity. Failing to implement patch management can leave computer systems and networks vulnerable to security breaches, resulting in devastating consequences. The implementation of patch management involves acquiring, testing, and installing software updates or patches to address vulnerabilities or issues in software applications. Best practices for patch management include developing a patch management policy, prioritizing patches based on criticality, testing patches before deployment, automating patch management where possible, establishing a patch management team, and maintaining an inventory of hardware and software.
FAQs
- What is patch management? Patch management is the process of acquiring, testing, and installing software updates or patches to address vulnerabilities or issues in software applications.
- Why is patch management important? Patch management is important because it helps to ensure that software applications are up to date and secure. Failing to implement patch management leaves systems vulnerable to security breaches, which could have disastrous consequences.
- What are the risks of not implementing patch management? Some of the risks of not implementing patch management include cyber attacks, data breaches, legal consequences, and reputation damage.
- What are the best practices for patch management? Best practices for patch management include developing a patch management policy, prioritizing patches based on criticality, testing patches before deployment, automating patch management where possible, establishing a patch management team, and maintaining an inventory of hardware and software.
- What is the role of cybersecurity professionals in patch management? Cybersecurity professionals are responsible for identifying vulnerabilities, testing patches, and ensuring that patches are deployed promptly. They should also monitor systems and applications for any signs of unauthorized access or security breaches.

by Mark | May 26, 2019 | How To, Patch Management, SCCM
How to update to SCCM 1902
Microsoft System Center Configuration Manager (SCCM) is a powerful tool used by organizations to manage their IT infrastructure. SCCM allows IT administrators to manage operating systems, applications, and updates on a large number of devices. With the release of SCCM 1902, Microsoft has added new features and improvements to the software. If you are using an older version of SCCM, it is important to update to SCCM 1902 to take advantage of these new features.
In this article, we will provide you with a step-by-step guide on how to update to SCCM 1902.
SCCM 1902 New Features
- Cloud Value
- Cloud Management Gateway (CMG) can be associated with boundary groups – Cloud Management Gateway deployments can now be associated with boundary groups to allow clients to default or fallback to the CMG for client communication according to boundary group relationships.
- Stop cloud service when it exceeds threshold – Configuration Manager can now stop a cloud management gateway (CMG) service when the total data transfer goes over your limit.
- Application Management
- Improvements to application approvals via email – When users request applications from Software Center, the email notification will now include their comments.
- Configuration Manager console
- Improvements to Configuration Manager console – Based on customer feedback aka the Cabana sessions at the Midwest Management Summit (MMS) Desert Edition 2018, this release includes several improvements to the Configuration Manager console.
- View recently connected consoles – You can now view the most recent connections for the Configuration Manager console. The view includes active connections and those that recently connected.
- View first monitor only during Configuration Manager remote control session – When connecting to a client with two or more monitors, a remote tools operator can now choose between seeing all monitors and the first monitor only.
- Search device views using MAC address – you can now search for a MAC address in a device view of the Configuration Manager console.
- Software Center
- Replace toast notifications with dialog window – When deployments need a restart or software changes are required, you now have the option of using a more intrusive dialog window to replace toast notifications on the client
- Configure default views in Software Center – You can now customize your end user’s default application layout and default application filter in Software Center.
- OS Deployment
- Improvements to task sequence media creation – When you create task sequence media, you can now customize the location that the site uses for temporary storage of data and add a label to the media.
- Improvements to Run PowerShell Script task sequence step – The Run PowerShell Script task sequence step now allows you to specify a timeout value, alternate credentials, a working directory and success codes.
- Import a single index of an Operating System Image – When importing a Windows image (WIM) file to Configuration Manager, you can now specify to automatically import a single index rather than all image indexes in the file.
- Progress status during in-place upgrade task sequence – You now see a more detailed progress bar during a Windows 10 in-place upgrade task sequence.
- Client Management
- Client Health Dashboard – You can now view a dashboard with information about the client health of your environment. View your client health, scenario health, common errors along with breakdowns by operating system and client versions.
- Specify a custom port for peer wakeup – You can now specify a custom port number for wake-up proxy.
- Real-time management
- Run CMPivot from the central administration site – Configuration Manager now supports running CMPivot from the central administration site in a hierarchy.
- Edit or copy PowerShell scripts – You can now Edit or Copy an existing PowerShell script used with the Run Scripts feature.
- Phased deployments
- Dedicated monitoring for phased deployments – Phased deployments now have their own dedicated monitoring node, making it easier to identify phased deployments you have created and navigate to the phased deployment monitoring view.
- Improvement to phased deployment success criteria – Specify additional criteria for the success of a phase in a phased deployment. Instead of only a percentage, these criteria can now also include the number of devices successfully deployed.
- Office Management
- Integration with analytics for Office 365 ProPlus readiness – Use Configuration Manager to identify devices with high confidence that are ready to upgrade to Office 365 ProPlus.
- Additional languages for Office 365 updates – Configuration Manager now supports all supported languages for Office 365 client updates.
- Office products on lifecycle dashboard – The product lifecycle dashboard now includes information for installed versions of Office 2003 through Office 2016.Redirect Windows known folders to OneDrive – Use Configuration Manager to move Windows known folders to OneDrive for Business. These folders include Desktop, Documents, and Pictures.
- OS servicing
- Optimized image servicing – When you apply software updates to an OS image, there’s a new option to optimize the output by removing any superseded updates.
- Specify thread priority for feature updates in Windows 10 servicing – Adjust the priority with which clients install a feature update through Windows 10 servicing.
Simplification
- Management insight rules for collections – Management insights has new rules with recommendations on managing collections. Use these insights to simplify management and improve performance.
- Distribution Point Maintenance Mode – You can now set a distribution point in maintenance mode. Enable maintenance mode when you’re installing software updates or making hardware changes to the server.
- Configuration Manager Console Notifications – To keep you better informed so that you can take the appropriate action, the Configuration Manager console now notifies you when lifecycle and maintenance events occur in the environment.
- In-console documentation dashboard – There is a new Documentation node in the new Community workspace. This node includes up-to-date information about Configuration Manager documentation and support articles.
SCCM 1902 FAQs
| Question |
Answer |
What is SCCM 1902?
|
SCCM 1902 is the latest version of System Center Configuration Manager, released by Microsoft in March 2019. |
What are the new features in SCCM 1902?
|
SCCM 1902 comes with several new features, including the ability to deploy Win32 applications using Intune, improved device compliance, and enhanced cloud management. |
What are the system requirements for SCCM 1902?
|
Operating System Requirements
- Windows Server 2012 R2 or later
- Windows 10 (Professional, Enterprise, or Education)
- Windows 8.1 (Professional or Enterprise)
- Windows 7 SP1 (Professional, Enterprise, or Ultimate)
Hardware Requirements
- Processor: 64-bit processor with at least 4 cores
- RAM: 8 GB of RAM or higher
- Hard disk space: 500 GB or higher (depending on the size of the environment)
- Network: 1 Gbps network adapter or faster
Software Requirements
- Microsoft SQL Server 2012 SP4 or later
- Microsoft .NET Framework 4.5.2 or later
- Windows ADK 10 version 1809 or later (for deploying Windows 10)
|
Can I upgrade to SCCM 1902 from an older version?
|
Yes, you can upgrade to SCCM 1902 from an older version, but you need to follow the upgrade path and ensure that your infrastructure meets the prerequisites for the upgrade. |
How do I upgrade to SCCM 1902?
|
You can upgrade to SCCM 1902 using the SCCM Console or command line, following a step-by-step process that includes downloading the update, running the prerequisite check, installing the update, and monitoring the progress.
Follow the guide below showing the exact steps to perform the upgrade |
How long does it take to upgrade to SCCM 1902?
|
The time required to upgrade to SCCM 1902 depends on the size and complexity of your SCCM infrastructure, but it typically takes a few hours to complete the upgrade process. |
What should I do after upgrading to SCCM 1902?
|
After upgrading to SCCM 1902, you should verify that your infrastructure is running the latest version, review and update your configuration settings, and test your SCCM infrastructure to ensure that all components are working correctly. |
Where can I find more information about SCCM 1902?
|
You can find more information about SCCM 1902 in the Microsoft documentation, including release notes, installation guides, and troubleshooting guides. |
SCCM 1902 Upgrade Process
Now, to upgrade to SCCM 1902 is quite an easy process, just follow these tasks below:
As with any upgrade or update, make sure you have an easy roll back position should anything cause an issue, either make sure you have a last known good backup or take a snapshot of your SCCM server prior to applying this update;
- Open your Configuration Manager Console and navigate to the Administration tab.

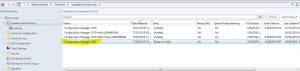
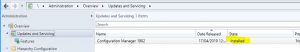
- Next we need to see if configuration manager has downloaded the SCCM 1902 update. Go click on Updates and Servicing and in the right side window, see if you have the update available.

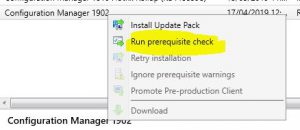
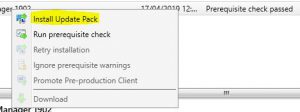
- Now we need to check the SCCM 1902 prerequisites are met before install this update. Right click the Configuration Manager 1902 update and choose Run Prerequisite Check.

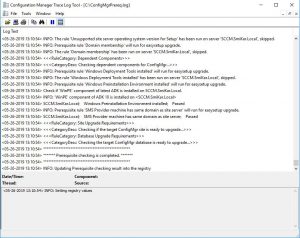
- The prerequisite check will run in the background. Keep refreshing your SCCM console to see the status of the check.

You can also check the ConfigMgrPrereq.log located in your SCCM Server’s C Drive for further details of the sccm 1902 prerequisite check.

This may take some time (around ten minutes) so go grab a coffee or a cup of tea while you wait and hopefully when you come back and refresh your configuration manager console you see
Prerequisite Check Passed

- Now on to the fun stuff, upgrade your configuration manager environment to SCCM 1902.
Right click the Configuration Manager 1902 update and choose Install Update Pack.

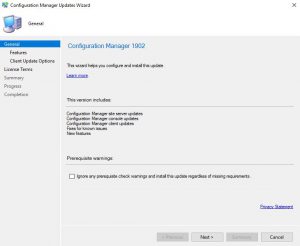
- The Configuration Manager Update Wizard now presents, ready for you to start the SCCM 1902 upgrade process. Click on Next to continue.

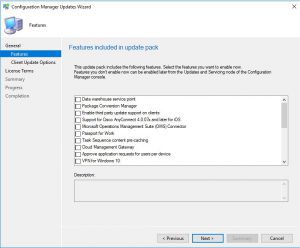
- We are now prompted with the features we wish to upgrade or install as part of this update. Carefully choose which features you need then click Next.

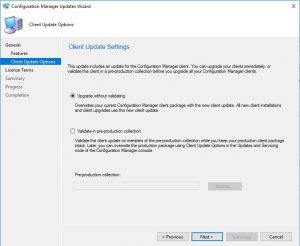
- If you have a preproduction collection to test the upgrade before deploying to your production collections, you can choose to do so on this screen. As this is one of our test labs, we wont go ahead with that and deploy this straight to production.

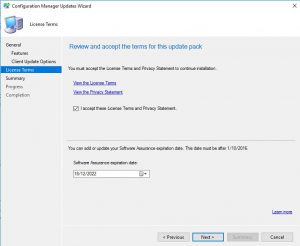
- You can review the license terms and conditions on this tab, make sure to check the checkbox to accept the terms of the license and then click Next.

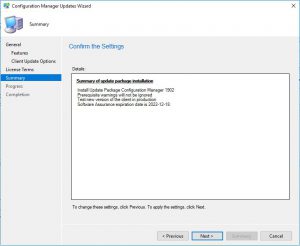
- Make sure on the Summary page that you have all the options you wish to upgrade or install displayed here, then click Next.
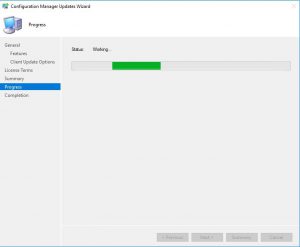
When you click next this will now start the upgrade process for SCCM.

- Now the SCCM 1902 upgrade will start the update process.

- The last screen is your completion screen, dont be fooled that it says completed, the update is still running and updating your SCCM infrastructure in the background.

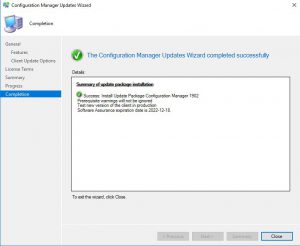
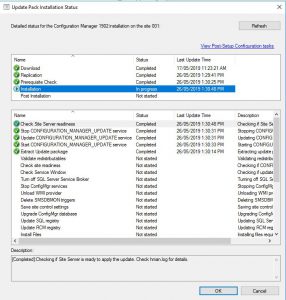
- To monitor the updates progress, go to the Monitoring tab, then Updates and Servicing Status. Choose the Configuration Manager 1902 update, then right click this then Show Status. From here, highlight Installation to watch the install status.

In the above picture you can see that our SCCM environment is still installing the update.
The update process may take some time, expect around 30 minutes.
- Finally, after some time and the update process was successful, you should be able to see in the configuration manager console, that Configuration Manager 1902 has a state of Installed.

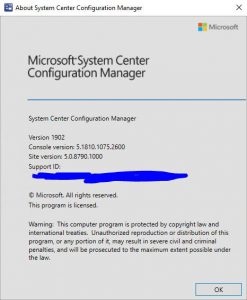
You can also click About Configuration Manager under the drop down arrow in the top left corner of the configuration manager console to see what version you are running. If everything was successful, you should see the version of your SCCM now showing 1902.

While you are here, dont forget to check out our software.
SnaPatch, which integrates with SCCM, VMware and HyperV to automate a snapshot then deploy patches to your virtual fleet.
SnapShot Master also integrates with VMware and HyperV and allows you to schedule snapshot creations then deletions.
Our Azure Management tools, that make your life easier to deploy, delete, shutdown and startup with orchestration of your Azure IAAS enviroment.
And finally, CARBON which replicates your Azure VMs back to your on-premise infrastructure with a simple few clicks.

by Mark | Dec 18, 2018 | Patch Management, Patch Releases, Security
Adobe Flash compromised

Adobe Flash Vulnerability Compromises Cybersecurity
Adobe officials have confirmed that a critical vulnerability has been discovered in Flash version 19.0.0.207, which was just released on Tuesday. Security researchers warn that this vulnerability, identified as CVE-2015-7645, is being exploited by attackers to surreptitiously install malware on end-users’ computers, even in fully-patched versions of the software.
Zero-Day Exploits
The critical security flaw is reportedly being used exclusively by Pawn Storm, a group that is targeting only government agencies as part of a broader, long-running espionage campaign. However, it’s common for these kinds of zero-day exploits to be distributed more widely once the element of surprise has waned. The vulnerability has been found in Flash versions 19.0.0.185 and 19.0.0.207, as well as potentially earlier versions. At present, no further technical details are available.
Recent Attacks
In the most recent attacks, links were sent via email that purported to contain information on current events. These URLs hosted the exploit, leading users to download the malware without realizing it. The following topics were used as bait in these attacks:
• “Suicide car bomb targets NATO troop convoy Kabul”
• “Syrian troops make gains as Putin defends air strikes”
• “Israel launches airstrikes on targets in Gaza”
• “Russia warns of response to reported US nuke buildup in Turkey, Europe”
• “US military reports 75 US-trained rebels return Syria”
How to Stay Safe
In light of this vulnerability, it’s essential to take steps to stay safe while using Flash. First, ensure that you have updated to the latest version of Flash Player to reduce the risk of an attack. It’s also important to avoid clicking on links or downloading attachments from suspicious emails or websites. If you receive an email with an unsolicited link or attachment, delete the message immediately. Finally, consider disabling Flash altogether, particularly if you don’t use it often.
Conclusion
The recent discovery of a critical security flaw in Adobe Flash is a cause for concern, particularly as attackers have already been exploiting it in targeted attacks. As such, it’s essential to stay vigilant and take steps to protect yourself against this and other vulnerabilities. By staying up-to-date with the latest software updates, being wary of suspicious emails and attachments, and disabling Flash if necessary, you can help ensure that your computer remains secure.

by Mark | Dec 18, 2018 | Patch Management, Patch Releases
Automate Patch Management with SnaPatch
Patch management doesn’t have to feel like a gamble. If you’re still relying on manual processes, you’re exposing your systems to unnecessary risks. SnaPatch streamlines patching for SCCM environments by combining automation, snapshot protection, and alerts to keep your infrastructure secure.
Why Manual Patch Management Is Risky
Every month brings new vulnerabilities via Microsoft’s Patch Tuesday. Without proper testing and automation, deploying patches manually can be time-consuming and risky—especially in environments with custom or sensitive server configurations. Missed patches or failed updates could lead to outages or security gaps.
Many IT teams use testing environments to simulate patch impact before rolling out updates. But when time or resources are tight, User Acceptance Testing (UAT) gets skipped, and patches go live untested—opening the door to potential issues.
Introducing SnaPatch
SnaPatch is a powerful add-on for Microsoft SCCM that automates patch deployment while giving you a rollback safety net. It creates snapshots of your VMs before patches are applied, and if something goes wrong, you can easily revert the changes. After a defined time, those snapshots are automatically deleted to free up storage.

SnaPatch also provides real-time email notifications so you’re always in the loop during patch deployment. From start to finish, you’ll have visibility, control, and peace of mind.
SnaPatch Benefits
- Automated snapshot creation and deletion around patch deployment
- Email notifications to track patch progress and outcomes
- Faster recovery in case a patch causes system failure
- Less time spent on UAT and manual intervention
- Greater consistency and compliance across environments
The Bottom Line
Patch management may never be fun, but it can be fast, safe, and reliable. With SnaPatch, you take the risk out of patching and put time back in your day. Don’t roll the dice—automate your patching strategy and protect your VMs with SnaPatch.
→ Learn more about SnaPatch

by Mark | May 27, 2017 | How To, Microsoft HyperV, Patch Management, SCCM, VMWare
Automate Snapshot Creation Before Deployment
Reduce Patching Risks with SnaPatch
System administrators are responsible for ensuring the smooth functioning of their organization’s computer systems. They are the ones who deploy new software and updates, perform maintenance tasks, and troubleshoot any issues that arise. However, keeping these systems up-to-date can be a daunting task, especially when new updates and patches are released frequently. This is where taking a snapshot before patching comes into play.
A snapshot before patching is a crucial tool that system administrators can use to protect their systems from vulnerabilities. In this article, we will discuss why taking a snapshot before patching is essential and how it can help system administrators safeguard their systems.
What is a Snapshot Before Patching?
A snapshot before patching is a backup copy of your system’s current state. This copy can be used to restore your system to its previous state in case something goes wrong during the patching process. Taking a snapshot before patching ensures that you have a stable and reliable system to fall back on if the patching process fails.
Why is a Snapshot Before Patching Important?
Taking a snapshot before patching is essential for several reasons. Here are some of the main reasons why system administrators should make this a standard practice:
- Protects Against System Failure: Patching can sometimes cause system failures. Having a snapshot before patching ensures that you can quickly restore your system to its previous state in case of such failures.
- Provides a Safe Environment for Testing: Taking a snapshot before patching allows system administrators to test the patches in a safe environment. This ensures that any issues that arise during the testing process can be addressed before the patches are applied to the live system.
- Helps in Disaster Recovery: Snapshots can be used as part of a disaster recovery plan. In case of a disaster, snapshots can be used to restore your system to a previous state.
Best Practices for Using Snapshots Before Patching
Here are some best practices for using snapshots before patching:
Always Test Patches:
Test patches in a safe environment before applying them to the live system.
Schedule Regular Snapshots:
Schedule regular snapshots so that you always have an up-to-date backup of your system.
Name Your Snapshots:
Give your snapshots meaningful names so that you can easily identify them.
Store Snapshots Securely:
Store your snapshots in a secure location to prevent unauthorized access.
Snapshots Before Patching FAQs
What is the difference between a snapshot and a backup?
A snapshot is a point-in-time copy of your system, whereas a backup is a copy of your system’s data that is stored separately.
How often should I take a snapshot before patching?
It depends on your organization’s needs. However, it is a good practice to take a snapshot before each patching session.
Can I take a snapshot of a virtual machine?
Yes, you can take a snapshot of a virtual machine. In fact, taking snapshots of virtual machines is a common practice in virtualized environments.
What happens if I don’t take a snapshot before patching?
If you don’t take a snapshot before patching, you run the risk of losing important data or causing system failures.
How to Snapshot before deploying Patches.
How SnaPatch Can Help You Take Snapshots Before Patching
When it comes to taking snapshots before patching, it can be a time-consuming and manual process for system administrators. However, there is a tool that can simplify the process and make it more efficient: SnaPatch.
What is SnaPatch?
SnaPatch is a software application that interacts with your Microsoft System Centre Configuration Manager (SCCM) environment to pull in all your machine information. It uses SCCM as the source of truth for all your VM information.
Next, it interfaces with either your vCentre or System Centre Virtual Machine Manager (SCVMM), or both. It takes control of your VM environment, allowing it to create and delete snapshots of your VMs.
How does SnaPatch work?
SnaPatch simplifies the snapshot process by automating it. It creates a snapshot of any virtual machine before allowing it to be patched. If the snapshot fails, the VM will not receive updates and will be removed from the patching schedule. SnaPatch streamlines the process and frees up your time by automating the snapshot and patching processes, while keeping you updated on progress via email notifications.
How do you deploy SnaPatch?
Deploying SnaPatch is easy and straightforward. After installation, the application discovers your SCCM environment and allows you to configure various settings such as email notifications, snapshot creation, and patch deployment.
Why use SnaPatch?
SnaPatch helps you take snapshots before patching in a more efficient and streamlined manner. It complies with SOX regulations and minimizes risk, and its automated snapshot creation feature ensures that you can easily roll back updates if necessary, giving you peace of mind and more time to focus on other critical tasks.
Conclusion
In conclusion, taking snapshots before patching is a critical step in ensuring the security and stability of your systems. SnaPatch can help simplify and automate this process, allowing you to deploy Microsoft updates in your VM environment safely and efficiently. Try SnaPatch today and streamline your patching process!

by Mark | Mar 15, 2017 | Fixes, Patch Management, Patch Releases, SCCM, Security
MICROSOFT’S March 2017 PATCH RELEASES
Well after an absence last month of the usual Microsoft Patch Tuesday releases, Microsoft have bundled more in to this months release, with 18 Windows Updates for the month of March 2017.

See how you can remove the risk of patch deployment by adding SnaPatch to your SCCM patching infrastructure?
MS17-006 – Critical
Cumulative Security Update for Internet Explorer (4013073)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS17-007 – Critical
Cumulative Security Update for Microsoft Edge (4013071)
This security update resolves vulnerabilities in Microsoft Edge. These vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited these vulnerabilities could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS17-008 – Critical
Security Update for Windows Hyper-V (4013082)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if an authenticated attacker on a guest operating system runs a specially crafted application that causes the Hyper-V host operating system to execute arbitrary code. Customers who have not enabled the Hyper-V role are not affected.
MS17-009 – Critical
Security Update for Microsoft Windows PDF Library (4010319)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user views specially crafted PDF content online or opens a specially crafted PDF document.
MS17-010 – Critical
Security Update for Microsoft Windows SMB Server (4013389)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if an attacker sends specially crafted messages to a Microsoft Server Message Block 1.0 (SMBv1) server.
MS17-011 – Critical
Security Update for Microsoft Uniscribe (4013076)
This security update resolves vulnerabilities in Windows Uniscribe. The most severe of these vulnerabilities could allow remote code execution if a user visits a specially crafted website or opens a specially crafted document. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS17-012 – Critical
Security Update for Microsoft Windows (4013078)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if an attacker runs a specially crafted application that connects to an iSNS Server and then issues malicious requests to the server.
MS17-013 – Critical
Security Update for Microsoft Graphics Component (4013075)
This security update resolves vulnerabilities in Microsoft Windows, Microsoft Office, Skype for Business, Microsoft Lync, and Microsoft Silverlight. The most severe of these vulnerabilities could allow remote code execution if a user either visits a specially crafted website or opens a specially crafted document. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS17-014 – Important
Security Update for Microsoft Office (4013241)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS17-015 – Important
Security Update for Microsoft Exchange Server (4013242)
This security update resolves a vulnerability in Microsoft Exchange Outlook Web Access (OWA). The vulnerability could allow remote code execution in Exchange Server if an attacker sends an email with a specially crafted attachment to a vulnerable Exchange server.
MS17-016 – Important
Security Update for Windows IIS (4013074)
This security update resolves a vulnerability in Microsoft Internet Information Services (IIS). The vulnerability could allow elevation of privilege if a user clicks a specially crafted URL which is hosted by an affected Microsoft IIS server. An attacker who successfully exploited this vulnerability could potentially execute scripts in the user’s browser to obtain information from web sessions.
MS17-017 – Important
Security Update for Windows Kernel (4013081)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker runs a specially crafted application.
MS17-018 – Important
Security Update for Windows Kernel-Mode Drivers (4013083)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application that could exploit the vulnerabilities and take control of an affected system.
MS17-019 – Important
Security Update for Active Directory Federation Services (4010320)
This security update resolves a vulnerability in Active Directory Federation Services (ADFS). The vulnerability could allow information disclosure if an attacker sends a specially crafted request to an ADFS server, allowing the attacker to read sensitive information about the target system.
MS17-020 – Important
Security Update for Windows DVD Maker (3208223)
This security update resolves an information disclosure vulnerability in Windows DVD Maker. The vulnerability could allow an attacker to obtain information to further compromise a target system.
MS17-021 – Important
Security Update for Windows DirectShow (4010318)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow an information disclosure if Windows DirectShow opens specially crafted media content that is hosted on a malicious website. An attacker who successfully exploited the vulnerability could obtain information to further compromise a target system.
MS17-022 – Important
Security Update for Microsoft XML Core Services (4010321)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow information disclosure if a user visits a malicious website. However, in all cases an attacker would have no way to force a user to click a specially crafted link. An attacker would have to convince a user to click the link, typically by way of an enticement in an email or Instant Messenger message.
MS17-023 – Important
Security Update for Adobe Flash Player (4014329)
This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, Windows 10, and Windows Server 2016.
Now that you have made it this far, a quick shameless plug for our software portfolio. 🙂
SnaPatch – Patch Management Addon for Microsoft’s SCCM.
SnapShot Master – Take control of your virtual machine snapshots, works with both Hyper-V and Vmware.
Azure Virtual Machine Cloner – Quickly and easily clone your Azure VMs, you can even migrate your VMs between ARM and ASM.
Azure Virtual Machine Scheduler – Save money and schedule the shutdown and power on of your virtual machines within Microsoft’s Azure Cloud.
Azure Virtual Machine Deployer – Deploy VMs to Microsoft’s Azure cloud easily, without the need for powershell.