by Mark | Jun 19, 2016 | Patch Management, Patch Releases
The following seventeen Patch Tuesday updates / patches have been released by Microsoft for the June 2016 Update deployment.
Are you ready to start deploying and remove the patching risk using SnaPatch Patch Management Software?
MS16-063 – Critical
Cumulative Security Update for Internet Explorer (3163649)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-068 – Critical
Cumulative Security Update for Microsoft Edge (3163656)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than users with administrative user rights.
MS16-069 – Critical
Cumulative Security Update for JScript and VBScript (3163640)
This security update resolves vulnerabilities in the JScript and VBScript scripting engines in Microsoft Windows. The vulnerabilities could allow remote code execution if a user visits a specially crafted website. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited these vulnerabilities could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-070 – Critical
Security Update for Microsoft Office (3163610)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-071 – Critical
Security Update for Microsoft Windows DNS Server (3164065)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker sends specially crafted requests to a DNS server.
MS16-072– Important
Security Update for Group Policy (3163622)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker launches a man-in-the-middle (MiTM) attack against the traffic passing between a domain controller and the target machine..
MS16-073 – Important
Security Update for Windows Kernel-Mode Drivers (3164028)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application.
MS16-074 – Important
Security Update for Microsoft Graphics Component (3164036)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow elevation of privilege if a user opens a specially crafted application.
MS16-075 – Important
Security Update for Windows SMB Server (3164038)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to the system and runs a specially crafted application.
MS16-076 – Important
Security Update for Netlogon (3167691)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker with access to a domain controller (DC) on a target network runs a specially crafted application to establish a secure channel to the DC as a replica domain controller.
MS16-077– Important
Security Update for WPAD (3165191)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if the Web Proxy Auto Discovery (WPAD) protocol falls back to a vulnerable proxy discovery process on a target system.
MS16-078 – Important
Security Update for Windows Diagnostic Hub (3165479)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application.
MS16-079 – Important
Security Update for Microsoft Exchange Server (3160339)
This security update resolves vulnerabilities in Microsoft Exchange Server. The most severe of the vulnerabilities could allow information disclosure if an attacker sends a specially crafted image URL in an Outlook Web Access (OWA) message that is loaded, without warning or filtering, from the attacker-controlled URL.
MS16-080 – Important
Security Update for Microsoft Windows PDF (3164302)
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted .pdf file. An attacker who successfully exploited the vulnerabilities could cause arbitrary code to execute in the context of the current user. However, an attacker would have no way to force a user to open a specially crafted .pdf file.
MS16-081 – Important
Security Update for Active Directory (3160352)
This security update resolves a vulnerability in Active Directory. The vulnerability could allow denial of service if an authenticated attacker creates multiple machine accounts. To exploit the vulnerability an attacker must have an account that has privileges to join machines to the domain.
MS16-082 – Important
Security Update for Microsoft Windows Search Component (3165270)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow denial of service if an attacker logs on to a target system and runs a specially crafted application.
MS16-083 – Critical
Security Update for Adobe Flash Player (3167685)
This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, and Windows 10.

by Mark | Jun 12, 2016 | Patch Management
Assess your Security Risk
Are you aware of the potential security risks facing your business? Cyber threats are becoming increasingly sophisticated and can have a devastating impact on your company’s reputation and finances. In this article, we’ll show you how to assess your security risk and take steps to protect your business from harm.
Identifying Your Security Risks
To begin, you need to identify your security risks. Microsoft has a great tool that can help you do this. By filling out a simple form, you can assign a dollar value to each of the security risks your business faces. Microsoft provides examples for each of the items to help you make an accurate assessment.
The following are some of the potential risks you may face:
Accidental Data Leakage:
This can occur when employees accidentally share sensitive information, such as customer data, with unauthorized parties.
Malware:
This is a type of software designed to harm your computer system, steal your data, or take control of your devices.
Insider Threat:
This is a risk posed by employees or contractors who may intentionally or unintentionally compromise your security.
Identity Theft:
This is when someone steals personal information, such as social security numbers or bank account details, and uses it for fraudulent purposes.
Malicious Access of Data from Personal Devices:
This can occur when employees use personal devices to access company data, making it vulnerable to security breaches.
Weak Passwords:
This is when passwords are easy to guess or are reused across multiple accounts, making them vulnerable to hacking attempts.
Social Engineering:
This is a tactic used by attackers to trick employees into divulging sensitive information or performing actions that compromise security.
Loss/Corruption of Data:
This can occur due to hardware failures, power outages, or natural disasters, such as floods or fires.
Misconfigured Systems:
This can occur when systems are not configured correctly, leaving them vulnerable to attack.
Outdated Operating System:
This is when systems are not updated to the latest software, leaving them open to known vulnerabilities.
Lack of Encryption:
This is when sensitive data is not encrypted, leaving it vulnerable to theft.
Equipment Failures:
This can occur when hardware such as servers, routers, or switches, fail due to aging, misuse, or other factors.
Unpatched Vulnerabilities:
This is when known security vulnerabilities are not addressed, leaving your system open to attack.
Untrained Employees:
This is when employees lack the knowledge or training to identify security risks or take appropriate action.
Taking Action to Mitigate Risks
Once you’ve identified your security risks, you can take steps to mitigate them. One way to do this is by patching your servers to protect against known vulnerabilities. However, this can be a difficult process, especially if you lack adequate rollback capabilities in case of a problem with the deployed update.
That’s where SnaPatch can help. This software takes a snapshot of your virtual servers and only deploys updates if the snapshot is successful. If the snapshot fails, no updates are deployed. The process is automated, and you receive email updates during the snapshot and deployment.
Protect Your Business Today
Don’t wait until a security breach occurs to take action. Assess your security risk today and take steps to protect your business from potential harm. With the right tools and knowledge, you can safeguard your company’s reputation and finances against cyber threats.
While you are here, I came across a great page from Microsoft that will help you assess your security risk.
Fill out the form with a dollar value for each of the options you choose and it will help you see how each of these breaches of security cost your company lost revenue. (If your not sure of the $ value, Microsoft has some examples for each of the items and their associated costs.)
The threat risk assessment covers the following;
- Accidental Data Leakage
- Malware
- Insider Threat
- Identity Theft
- Malicious Access of data from personal devices
- Weak Passwords
- Social Engineering
- Loss/corruption of data
- Misconfigured Systems
- Outdated Operating System
- Lack of Encryption
- Equipment Failures
- Unpatched Vulnerabilities
- Untrained Empoyees
https://www.microsoft.com/security/security-risk-assessment/index.html?Ocid=C+E%20Social%20FY16_Social_TW_msftsecurity_20160610_489464562#/
If patching your server fleet is difficult to get approved through your change approval board, for lack of adequate roll back in case of an issue with a deployed update, SnaPatch can help. SnaPatch will take a snapshot of your virtual servers (Vmware of HyperV) and only if the snapshot is successful, will it then allow your existing System Centre Configuration Manager (SCCM) to deploy updates to those servers. If the snapshot isnt successful, then no updates are deployed. The whole process is automated with email updates during the snapshot and deployment. Find out more @ Smikar Software

by Mark | May 28, 2016 | Features, Patch Management, Patch Releases, SCCM
SCCM 1602 Upgrade
Microsoft released an update to SCCM from version 1511 to version 1602 a few months back.
Updating from SCCM 1511 to 1602 is a fairly easy process, you just need to follow the steps;
Go to your SCCM console, and then to Administration, Cloud Services, then Updates and Servicing.

Right click the update and choose to run the prerequisite check. This will take a few minutes, so give this sometime to complete then refresh the page and make sure there are no errors. Now to install 1602, again right click on the update, but this time choose Install Update Pack. It is a very easy upgrade process, you basically just need to follow the bouncing ball. The upgrade can take 10 – 30 minutes depending on your environment.
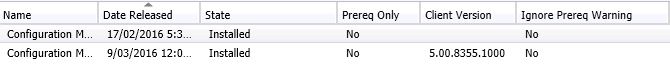
Once completed you can check your version number within SCCM by going to the top left hand corner, clicking the down arrow, then choosing About Configuration Manager. You can see, as in the picture below, the System Centre Configuration Manager version is on 1602.

Click the link to see how to install the next update, KB3155482
SCCM 1602 Features
SCCM version 1602 introduces some great new features as below;
- Client Online Status
- You can now view the online status of devices in Assets and Compliance. New icons indicate the status of a device as online or offline
- Support for SQL Server AlwaysOn Availability Groups
- Configuration Manager now supports using SQL Server AlwaysOn Availability Groups to host the site database
- Windows 10 Device Health Attestation Reporting
- You can now view the status of Windows 10 Device Health Attestation in the Configuration Manager console to ensure that the client computers have a trustworthy BIOS, TPM, and boot software
- Office 365 Update Management
- You can now natively manage Office 365 desktop client updates using the Configuration Manager Software Update Management (SUM) workflow. You can manage Office 365 desktop client updates just like you manage any other Microsoft Update
- New Antimalware Policy Settings
- New antimalware settings that can now be configured include protection against potentially unwanted applications, user control of automatic sample submission, and scanning of network drives during a full scan

by Mark | May 12, 2016 | Patch Management, Patch Releases
The following sixteen Patch Tuesday updates / patches have been released by Microsoft for the April 2016 Update deployment.
Are you ready to start deploying and remove the patching risk using SnaPatch Patch Management Software?
MS16-051 – Critical
Cumulative Security Update for Internet Explorer (3155533)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-052 – Critical
Cumulative Security Update for Microsoft Edge (3155538)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than users with administrative user rights.
MS16-053 – Critical
Cumulative Security Update for JScript and VBScript (3156764)
This security update resolves vulnerabilities in the JScript and VBScript scripting engines in Microsoft Windows. The vulnerabilities could allow remote code execution if a user visits a specially crafted website. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited these vulnerabilities could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-054 – Critical
Security Update for Microsoft Office (3155544)
This security update resolves vulnerabilities in Microsoft Office. The vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-055 – Critical
Security Update for Microsoft Graphics Component (3156754)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted document or visits a specially crafted website. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS16-056– Critical
Security Update for Windows Journal (3156761)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted Journal file. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS16-044 – Critical
Security Update for Windows OLE (3146706)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if Windows OLE fails to properly validate user input. An attacker could exploit the vulnerability to execute malicious code. However, an attacker must first convince a user to open either a specially crafted file or a program from either a webpage or an email message.
MS16-057 – Critical
Security Update for Windows Shell (3156987)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker successfully convinces a user to browse to a specially crafted website that accepts user-provided online content, or convinces a user to open specially crafted content. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-058 – Important
Security Update for Windows IIS (3141083)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker with access to the local system executes a malicious application. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-059 – Important
Security Update for Windows Media Center (3150220)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if Windows Media Center opens a specially crafted Media Center link (.mcl) file that references malicious code. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-060– Important
Security Update for Windows Kernel (3154846)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application.
MS16-061 – Important
Security Update for Microsoft RPC (3155520)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an authenticated attacker makes malformed Remote Procedure Call (RPC) requests to an affected host.
MS16-062 – Important
Security Update for Windows Kernel-Mode Drivers (3158222)
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application.
MS16-064 – Critical
Security Update for Adobe Flash Player (3157993)
This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, and Windows 10.
MS16-065 – Important
Security Update for .NET Framework (3156757)
This security update resolves a vulnerability in Microsoft .NET Framework. The vulnerability could cause information disclosure if an attacker injects unencrypted data into the target secure channel and then performs a man-in-the-middle (MiTM) attack between the targeted client and a legitimate server.
MS16-066 – Critical
Security Update for Virtual Secure Mode (3155451)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow security feature bypass if an attacker runs a specially crafted application to bypass code integrity protections in Windows.
MS16-067 – Critical
Security Update for Volume Manager Driver (3155784)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow information disclosure if a USB disk mounted over Remote Desktop Protocol (RDP) via Microsoft RemoteFX is not correctly tied to the session of the mounting user.

by Mark | Apr 13, 2016 | Patch Management, Patch Releases
The following thirteen Patch Tuesday updates / patches have been released by Microsoft for the April 2016 Update deployment.
Are you ready to start deploying and remove the patching risk using SnaPatch Patch Management Software?
MS16-037 – Critical
Cumulative Security Update for Internet Explorer (3148531)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-038 – Critical
Cumulative Security Update for Microsoft Edge (3148532)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than users with administrative user rights.
MS16-039 – Critical
Security Update for Microsoft Graphics Component (3148522)
This security update resolves vulnerabilities in Microsoft Windows, Microsoft .NET Framework, Microsoft Office, Skype for Business, and Microsoft Lync. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted document or visits a webpage that contains specially crafted embedded fonts.
MS16-040 – Critical
Security Update for Microsoft XML Core Services (3148541)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user clicks a specially crafted link that could allow an attacker to run malicious code remotely to take control of the user’s system. However, in all cases an attacker would have no way to force a user to click a specially crafted link. An attacker would have to convince a user to click the link, typically by way of an enticement in an email or Instant Messenger message.
MS16-041 – Important
Security Update for .NET Framework (3148789)
This security update resolves a vulnerability in Microsoft .NET Framework. The vulnerability could allow remote code execution if an attacker with access to the local system executes a malicious application.
MS16-042– Critical
Security Update for Microsoft Office (3148775)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-044 – Important
Security Update for Windows OLE (3146706)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if Windows OLE fails to properly validate user input. An attacker could exploit the vulnerability to execute malicious code. However, an attacker must first convince a user to open either a specially crafted file or a program from either a webpage or an email message.
MS16-045 – Important
Security Update for Windows Hyper-V (3143118)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if an authenticated attacker on a guest operating system runs a specially crafted application that causes the Hyper-V host operating system to execute arbitrary code. Customers who have not enabled the Hyper-V role are not affected.
MS16-046 – Important
Security Update for Secondary Logon (3148538)
This security update resolves a vulnerability in Microsoft Windows. An attacker who successfully exploited this vulnerability could run arbitrary code as an administrator.
MS16-047 – Important
Security Update for SAM and LSAD Remote Protocols (3148527)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker launches a man-in-the-middle (MiTM) attack. An attacker could then force a downgrade of the authentication level of the SAM and LSAD channels and impersonate an authenticated user.
MS16-048– Important
Security Update for CSRSS (3148528)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow security feature bypass if an attacker logs on to a target system and runs a specially crafted application.
MS16-049 – Important
Security Update for HTTP.sys (3148795)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow denial of service if an attacker sends a specially crafted HTTP packet to a target system.
MS16-050 – Important
Security Update for Adobe Flash Player (3154132)
This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, and Windows 10.

by Mark | Mar 29, 2016 | How To, Patch Management
Manually download updates with SCCM
In today’s fast-paced world, keeping up with the latest software updates is critical. With new features, bug fixes, and security patches being released every day, it’s essential to ensure that your systems are up to date. Microsoft’s System Center Configuration Manager (SCCM) is an enterprise-grade software management solution that allows you to deploy and manage software updates across your organization. In this article, we will explore how to manually download updates with SCCM to keep your systems up to date.
What is SCCM?
SCCM is a software management tool developed by Microsoft. It allows IT administrators to manage and deploy software updates, security patches, and other configuration changes across their organization’s Windows devices. SCCM provides a centralized console where administrators can view and manage all of their organization’s Windows devices and ensure that they are up-to-date with the latest software and security updates.
Why Use SCCM?
There are several benefits to using SCCM for software management:
- Centralized management: SCCM provides a centralized console for managing all Windows devices in an organization, making it easy to manage software updates and security patches across multiple devices.
- Automation: SCCM can automate the deployment of software updates and security patches, saving IT administrators time and ensuring that updates are consistently applied across all devices.
- Reporting: SCCM provides detailed reporting capabilities, allowing administrators to track which devices are up-to-date with the latest software and security updates.
Now that we’ve covered the basics of SCCM let’s dive into the process of manually downloading updates with SCCM.
Understanding SCCM Software Updates
Before we dive into how to manually download updates with SCCM, let’s first understand what software updates are and how SCCM handles them. Software updates are packages that contain updates to existing software, such as security patches, bug fixes, and feature enhancements. SCCM uses the Windows Server Update Services (WSUS) infrastructure to manage and deploy software updates.
WSUS is a server role that allows administrators to manage and distribute updates for Windows operating systems and other Microsoft software. SCCM uses WSUS to download software updates from Microsoft Update and distribute them to client computers in the organization. SCCM also allows administrators to create and deploy custom software updates to meet specific business needs.
Now that we have a basic understanding of how SCCM handles software updates let’s explore how to manually download updates with SCCM.
If you ever have the need to Manually Download Updates with SCCM (like with a zero day exploit deployment) I will show you how to below. This helps even if updates haven’t been downloaded automatically by the Auto Deployment Rule.

To kick off a manual download of updates with SCCM, follow these steps.
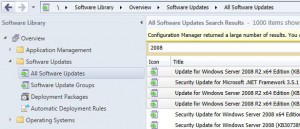
Open your SCCM console and go to Software Library, then expand Software Updates and then click on All Software Updates.

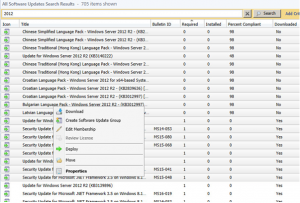
Let the list populate and select the updates that want to download, then right click and choose Download.

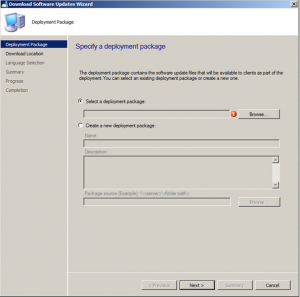
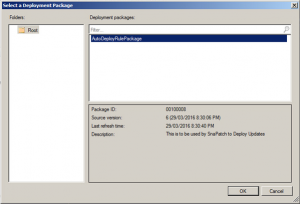
It will then prompt your to Select a Deployment Package. Click Browse.

Select the Auto Deployment Rule that you use for your monthly patch deployments and then click on OK.

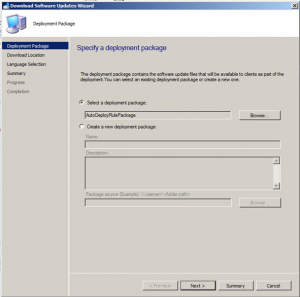
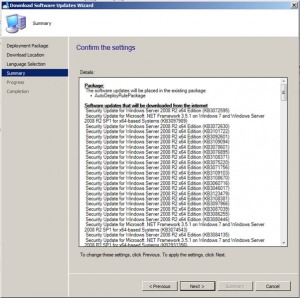
Once the deployment rule had been selected, click on Next.

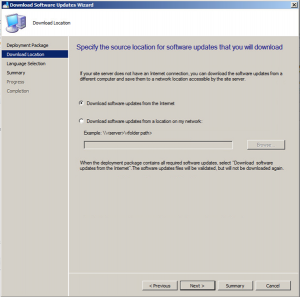
Now choose to Download software updates from the Internet.

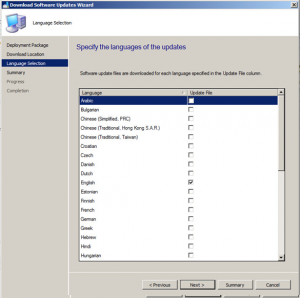
Choose the required update language then click Next.

Now you should be ready to download the updates you have selected. If ready to do so, click on Next.

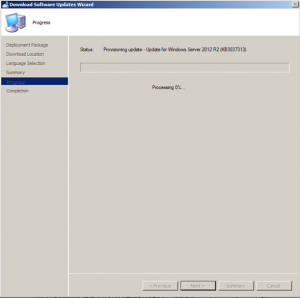
Your updates will start downloading. Note that this may take some time to complete the downloads.

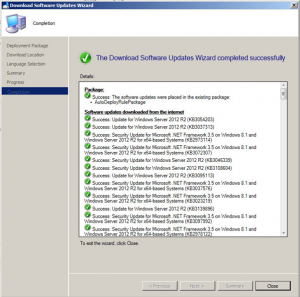
Hopefully all went well and your updates are now ready to be deployed.

This is a great way to download updates really quickly and make them available to deploy them to your desktops and servers. Click the link to see another great post on how to create a SCCM Automatic Deployment Rule.