
by Mark | Aug 26, 2016 | Errors, Patch Management, Patch Releases, Risk, Security
Windows 10 has been a reliable operating system for many users, but recently, some patches released by Microsoft have caused various issues. One of the latest problems is caused by KB3176934, which appears to break Windows 10 PowerShell. In particular, it affects the Desired State Configuration (DSC) functionality in PowerShell, rendering it useless.
What is KB3176934?
KB3176934 is a security update released by Microsoft in August. The patch was meant to fix some security issues with the operating system, but instead, it caused a problem with PowerShell. The issue is related to a missing .MOF file in the build package, causing the update to break DSC.
The Consequences of the Issue
The missing .MOF file leads to all DSC operations resulting in an “Invalid Property” error. This means that if you are using DSC on any Windows client, or from any Windows client, you should uninstall the update. The PowerShell function will be completely unusable until the KB3176934 update is removed.

Other Issues Caused by Recent Patches
This isn’t the only issue caused by the August releases of patches by Microsoft. Two other known issues were caused by security patches, namely Microsoft patches KB3177725 and KB3176493 causing printing issues, and Microsoft Patch KB3179575 causing authentication issues with Windows 2012 servers. Fortunately, a fix for the printing issue problem (KB3187022) has been released. Still, there has been no correspondence regarding the authentication issues, making it unclear whether a fix is coming soon.
How to Fix the PowerShell Issue
If you have experienced this issue on your Windows 10 machine, don’t worry. There is a solution, and it’s relatively easy to implement. The only way to fix this problem is to uninstall KB3176934 from the affected machine. Once you have removed the update, DSC functionality should be restored to PowerShell
Conclusion
If you use PowerShell for DSC, KB3176934 is a patch you need to avoid. While it’s essential to keep your operating system up to date, this update is not worth the trouble. The missing .MOF file breaks DSC functionality, leading to an “Invalid Property” error, rendering it useless. It’s crucial to stay aware of the latest updates from Microsoft and to remove any problematic ones as soon as possible.

by Mark | Aug 23, 2016 | Errors, Fixes, How To, Patch Releases
Microsoft Patch KB3179575 causing authentication issues with Windows 2012 servers
Seems yet another Microsoft security patch is causing issues this month. KB3179575 which was in the August Patch Tuesday deployment is to fix issues with the Windows 2012 (not R2) operating system.

Taken directly from the Microsoft site, this update includes quality improvements but no new operating system features are being introduced.
The key changes include:
- Addressed issue that required users to wait up to 30 seconds after booting-up, before the device was available and ready for use.
- Addressed issue that prevents the automatic deletion of old Dynamic Host Configuration Protocol (DHCP) backup files—Extensible Storage Engine (ESE) transaction logs.
- Addressed issue that caused Cluster service on remaining nodes to stop unexpectedly when a failover cluster node experiences a power outage.
- Addressed issue that causes a NFS service to stop responding on a two-node Windows cluster deployment, affecting clients to not be able reach an NFS share.
- Addressed issue after installing KB3146706 that causes Office 2010 to stop responding when Enhanced Mitigation Experience Toolkit (EMET) is enabled.
At this stage it seems to be only affecting logons (authentication) to Windows 2012 Domain Controllers, again at this stage the only fix is to uninstall this update, or if you deployed this security update using Microsoft’s SCCM and SnaPatch, you can roll this update deployment back. There is no known fix at this stage.
You may also be interested in some other Microsoft patches KB3177725 & KB3176493 which are known to cause printing issues. These two security patches were also released this month as well as KB3176934 breaks Windows 10 Powershell.

by Mark | Aug 11, 2016 | Fixes, Patch Management, Patch Releases, SCCM, Security
MICROSOFT’S August 2016 PATCH RELEASES
The following nine Patch Tuesday updates / patches have been released by Microsoft for the August 2016 Update deployment.
Are you ready to start deploying and remove the patching risk using SnaPatch Patch Management Software?
MS16-095 – Critical
Cumulative Security Update for Internet Explorer (3177356)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-096 – Critical
Cumulative Security Update for Microsoft Edge (3177358)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than users with administrative user rights.
MS16-097 – Critical
Security Update for Microsoft Graphics Component (3177393)
This security update resolves vulnerabilities in Microsoft Windows, Microsoft Office, Skype for Business, and Microsoft Lync. The vulnerabilities could allow remote code execution if a user either visits a specially crafted website or opens a specially crafted document. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS16-098– Critical
Security Update for Windows Kernel-Mode Drivers (3178466)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application that could exploit the vulnerabilities and take control of an affected system.
MS16-099 – Critical
Security Update for Microsoft Office (3177451)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-100 – Important
Security Update for Secure Boot (3179577)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow security feature bypass if an attacker installs an affected boot manager and bypasses Windows security features.
MS16-101 – Important
Security Update for Windows Authentication Methods (3178465)
This security update resolves multiple vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow elevation of privilege if an attacker runs a specially crafted application on a domain-joined system.
MS16-102 – Critical
Security Update for Microsoft Windows PDF Library (3182248)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user views specially crafted PDF content online or opens a specially crafted PDF document. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-103– Important
Security Update for ActiveSyncProvider (3182332)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow information disclosure when Universal Outlook fails to establish a secure connection.

by Mark | Jul 28, 2016 | Features, How To, Patch Releases, SCCM
SCCM 1606 Update
So what was the most exciting thing released this month? Well if you said Pokemon GO, you are on the wrong blog.

It was in fact the release of a well received update to System Centre Configuration Manager, known as update SCCM 1606.
SCCM 1606 (released on the 22nd of July 2016) introduces some great new features to an already excellent product by Microsoft. Particularly new enhancements in application management, deployment and provisioning, the experience of the end user, security and data protection and content distribution. Administrators that use SCCM in a hybrid mode with Microsoft Intune receive additional functionality. This update also includes support for the Windows 10 Anniverary update.
Exciting New Features of SCCM 1606
SCCM 1606 includes enhancements to application management, deployment and provisioning, end-user experience, security, data protection, and content distribution. If you’re using SCCM in hybrid mode with Microsoft Intune, this update provides additional functionality. Additionally, it includes support for the Windows 10 Anniversary update. Here’s a quick overview of some of the new features:
Windows Information Protection:
Create and deploy information protection policy, including choosing your protected apps and defining your EDP-protection level.
Windows Defender Advanced Threat Protection:
On-board and off-board Windows 10 clients to the cloud service and view agent health in the monitoring dashboard (requires a Windows Defender ATP tenant in Azure).
Windows Store for Business Integration:
Manage and deploy applications purchased through the Windows Store for Business portal for both online and offline licensed apps.
Windows Hello for Business policies:
Set policies for domain-joined Windows 10 devices managed by the Configuration Manager client
SCCM 1606 FAQs
| Question |
Answer |
What is SCCM 1606?
|
SCCM 1606 is a well-received update to System Centre Configuration Manager, released on July 22nd, 2016. It introduces new features to an already excellent product by Microsoft. |
What are the new features introduced in SCCM 1606?
|
SCCM 1606 introduces new enhancements in application management, deployment and provisioning, the experience of the end user, security and data protection, and content distribution. |
What are the enhancements in application management?
|
SCCM 1606 includes Windows Information Protection features that allow you to create and deploy information protection policies, including the ability to choose protected apps and define protection levels. |
What are the enhancements in deployment and provisioning?
|
SCCM 1606 includes Windows Defender Advanced Threat Protection features that enable the ability to onboard and off-board Windows 10 clients to the cloud service and view agent health in the monitoring dashboard. |
What are the enhancements in end-user experience?
|
SCCM 1606 includes Windows Store for Business Integration, allowing you to manage and deploy applications purchased through the Windows Store for Business portal for both online and offline licensed apps, as well as Windows Hello for Business policies for domain-joined Windows 10 devices managed by the Configuration Manager client. |
What are the enhancements in security and data protection?
|
SCCM 1606 includes Windows Information Protection features for creating and deploying information protection policies. |
What are the enhancements in content distribution?
|
SCCM 1606 includes Windows Store for Business Integration for managing and deploying applications purchased through the Windows Store for Business portal. |
What is the process for updating to SCCM 1606?
|
To update to SCCM 1606, ensure you have a recent backup or snapshot prior to upgrading the system. Then, highlight the SCCM 1606 update, right-click, and choose Run Prerequisite Check. Once the prerequisite check passes, highlight the SCCM 1606 update again, right-click, and choose Install Update Pack. Follow the prompts to complete the installation. |
How can I check the status of the SCCM 1606 update download?
|
You can check the download status by looking into the dmpdownloader.log file. |
What should I do if the SCCM 1606 update download freezes?
|
If the download freezes, refresh the console, and if the update is still shown as downloading, restart the SMS_EXECUTIVE service. |
How can I view the ConfigMgrPrereq.log file?
|
The ConfigMgrPrereq.log file should be located in the root of your C Drive. |
What should I do if there are issues with the prerequisite check?
|
If there are issues with the prerequisite check, review the ConfigMgrPrereq.log file to troubleshoot the issue. |
Can I deploy the SCCM 1606 update to Pre-Production environments?
|
Yes, you can select to deploy the client update to Pre-Production environments before doing a full-scale deployment to Production. |
How long will the SCCM 1606 installation take?
|
The installation process will take some time, so be patient. Once completed, you will see the update has been completed, and you can click on CLOSE. |
Updating SCCM to 1606
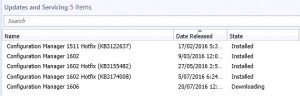
If you cannot see the SCCM 1606 update in your console (go to Administration, then expand Cloud Services, then highlight Updates and Servicing there is an available powershell script you can run that is supplied by Microsoft to kick off the download. (SCCM 1606 Powershell script here).

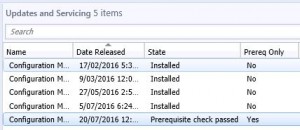
As in the above picture, you can see that the 1606 update is still downloading. You can check to see the download status, by looking in to the dmpdownloader.log.

There have been some reports of the download freezing. If after sometime you refresh the console and the update is still shown as downloading, restart the SMS_EXECUTIVE service.
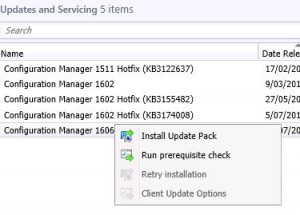
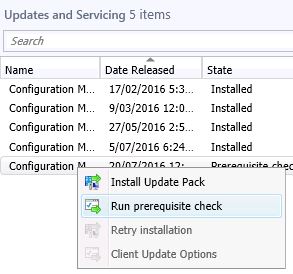
Once the update has downloaded, you can start to plan for the update process. As always, make sure you have a recent backup or snapshot prior to upgrading the system, then highlight the SCCM 1606 update, RIGHT CLICK and choose Run Prerequisite Check.

Give SCCM some time to verify the update is suitable for your environment. You can view the ConfigMgrPrereq.log file (should be located in the root of your C Drive) to see if there are any issues.


Once you see Prerequisite Check Passed , again highlight the SCCM 1606 update, RIGHT CLICK and then choose Install Update Pack.

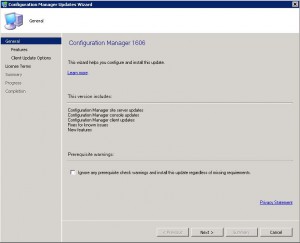
Now we start the installation. Click on NEXT.

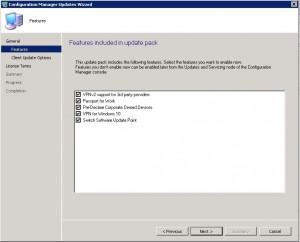
Next you have the option to install
- VPNv2 support for third party providers
- Passport for Work
- Pre-Declare Corporate Owned Devices
- VPN for Windows 10
- Switch Software Update Point
Choose the options you wish to install then click NEXT.

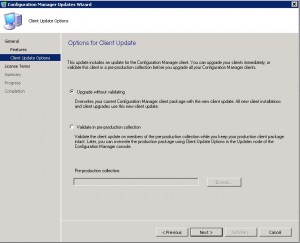
If you have a Pre-Production environment you can select to deploy the client update to them before you do a full scale deployment to Production. As this is one of our many test labs, Ill choose to Upgrade without Validating. Click on NEXT.

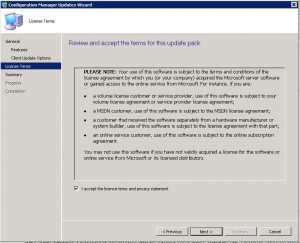
Accept the license terms and click NEXT

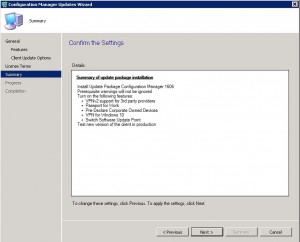
On the Summary Tab, check that you are happy with the selection then click on NEXT again to proceed to then start the installation.

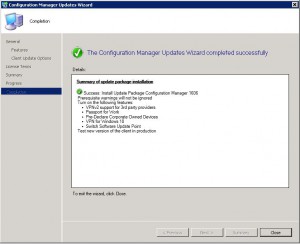
All going well, the progress of the installation will take some time, so be patient. You should finally see the update has now been completed and can click on CLOSE

Conclusion
SCCM 1606 provides an impressive set of new features, making it a valuable tool for managing applications and deployments. The update process is straightforward, but it’s always important to ensure you have a recent backup or snapshot prior to upgrading the system. If you’re looking for a robust solution to manage your organization’s systems, SCCM is definitely worth considering.

by Mark | Jul 13, 2016 | How To, Patch Management, Patch Releases, Security
The following eleven Patch Tuesday updates / patches have been released by Microsoft for the July 2016 Update deployment.
Are you ready to start deploying and remove the patching risk using SnaPatch Patch Management Software?
MS16-084 – Critical
Cumulative Security Update for Internet Explorer (3169991)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-085 – Critical
Cumulative Security Update for Microsoft Edge (3169999)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than users with administrative user rights.
MS16-086 – Critical
Cumulative Security Update for JScript and VBScript (3169996)
This security update resolves a vulnerability in the JScript and VBScript scripting engines in Microsoft Windows. The vulnerability could allow remote code execution if a user visits a specially crafted website. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerabilities could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-087– Critical
Security Update for Windows Print Spooler Components (3170005)
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if an attacker is able to execute a man-in-the-middle (MiTM) attack on a workstation or print server, or set up a rogue print server on a target network.
MS16-088 – Critical
Security Update for Microsoft Office (3170008)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-089– Important
Security Update for Windows Secure Kernel Mode (3170050)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow information disclosure when Windows Secure Kernel Mode improperly handles objects in memory.
MS16-090 – Important
Security Update for Windows Kernel-Mode Drivers (3171481)
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application that could exploit the vulnerabilities and take control of an affected system.
MS16-091 – Important
Security Update for .NET Framework (3170048)
This security update resolves a vulnerability in Microsoft .NET Framework. The vulnerability could cause information disclosure if an attacker uploads a specially crafted XML file to a web-based application.
MS16-092– Important
Security Update for Windows SMB Server (3164038)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to the system and runs a specially crafted application.
MS16-093 – Important
Security Update for Adobe Flash Player (3174060)
This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows RT 8.1, Windows Server 2012 R2, and Windows 10.
MS16-094– Important
Security Update for Secure Boot (3177404)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow Secure Boot security features to be bypassed if an attacker installs an affected policy on a target device. An attacker must have either administrative privileges or physical access to install a policy and bypass Secure Boot.
See how SnaPatch can help and remove the risk of Patch Tuesday updates.

by Mark | Jul 5, 2016 | Deployment, How To, Patch Management, Patch Releases, Risk, SCCM, Security
Deploying a Zero Day Exploit Fix with Microsoft SCCM 2012
Zero Day exploits are vulnerabilities that are found and can be used by hackers to exploit and use for malicious or personal intent. These exploits have been known to affect both software and hardware, causing issues to programs, data, computers, and networks. Once a patch or fix is released by the vendor, the issue is no longer known as a Zero Day vulnerability. In this article, we will discuss how to remediate Zero Day attacks and how to deploy a Zero Day exploit fix using Microsoft SCCM
Remediating Zero Day Attacks
Unfortunately, there isn’t much that can be done until a fix or update is released that patches the security hole. Once a patch is released, it is best to deploy and apply the patch as soon as possible. To reduce the risk of unknown vulnerabilities, it is good practice to keep your hardware and software up to date. This will remove any previously found vulnerabilities from your environment as patches are applied. Having a patching process in place and suitable infrastructure to do so (e.g., Microsoft SCCM and SnaPatch) where you can deploy updates easily and often are also good practices.
Deploying a Zero Day Exploit Patch Using SCCM
Unfortunately, there isn’t much that can be done until a fix or update is released that patches the security hole. Once a patch is released, it is best to deploy and apply the patch as soon as possible. To reduce the risk of unknown vulnerabilities, it is good practice to keep your hardware and software up to date. This will remove any previously found vulnerabilities from your environment as patches are applied. Having a patching process in place and suitable infrastructure to do so (e.g., Microsoft SCCM and SnaPatch) where you can deploy updates easily and often are also good practices.
Zero Day Exploit Overview
So what exactly is a Zero Day Exploit you ask? To be exact, a Zero Day Exploit is a vulnerability that is found that a possible Hacker can use to exploit and use for malicious or personal intent. The Vendor (software or hardware) has Zero Days to plan, mitigate and fix the issue so that there is no further exploitation of the vulnerability. The exploits have been known to be for either software (Operating Systems and Software) and hardware. They have been known to cause issues to programs, data, computers and to the network.

Zero Day Attack Timeline
In the case of a breach being found in some software, a Zero Day Exploit normally follows this;
- A hacker finds a vulnerability with a product (software/hardware).
- The hacker writes an exploit and uses it either to be malicious or financial gain.
- Exploit is detected either by Users, Security Companies or the Vendor themselves.
- The Vendor studies the new exploit and develops a fix.
- The Vendor releases a new patch to fix the exploit
- Users install the Patch or Virus Definition update.
The biggest issue with a Zero Day Exploit is that they are generally unknown until they have been used to breach systems, leaving everyone vulnerable until the Vendor releases security advice on how to remediate the issue or a patch or update. This could be days, weeks, months or even years before the Vendor learns of the vulnerability. Once a Patch or Fix has been released by the Vendor, then the issue is no longer known as a Zero Day Vulnerability.
How to remediate Zero Day Attacks
Unfortunately there isnt much that can be done until there is a fix or update released that patches the security hole. Once a patch is released it is best to deploy and apply the patch as soon as is possible.
To also reduce the risk, it is good practice which will aid you in mitigation of vulnerabilities that are unknown to yourself if you keep your hardware and software patched up to date. This will remove from your environment any previously found vulnerabilities as patches are applied. Having a Patching Process in place and suitable infrastructure to do so (ie Microsoft SCCM and SnaPatch for instance) where you can deploy updates easily and often are also good practice.
Using SCCM to deploy a Zero Day Exploit Patch
If you are using Microsofts SCCM 2012, you can easily deploy an update that addresses a Zero Day Vulnerability by following these steps;
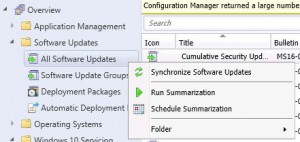
- Log on to your SCCM console, then go to Software Library, then expand Software Updates and highlight All Software Upates. Now Right Click and choose Synchronise Software Updates. This will synchronise your SCCM server with your WSUS updates server. Allow a few minutes for the new updates to populate the view. You can check the Wsyncmgr.log to view the update synchronisation.

- If you know the Bulletin ID number (the update number released by Microsoft in the format MSXX-XXX. In this example I am choosing MS16-082), you can now search for this within the console.

- Make sure that the update has downloaded and if not, right click the update and choose Download. You will obviously need to give the update sometime to download in to your environment and be ready for deployment. Click this link to see how to manually download updates if you dont know how.

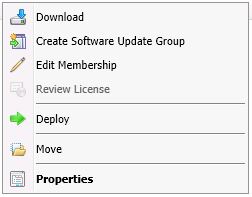
- When the update is downloaded and ready for deployment, you are now ready to deploy the Update. (If you are using SnaPatch to deploy the updates, go straight to the SnaPatch Section below.)
Right Click the update (or updates) and choose Deploy.
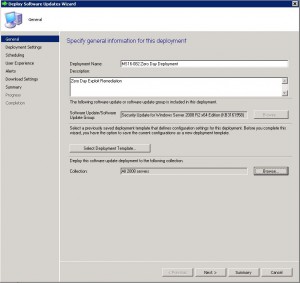
Enter in a Deployment Name, a Description, and choose the collection you wish the Zero Day exploit to deploy to. Once you have chosen the correct settings, click on Next.
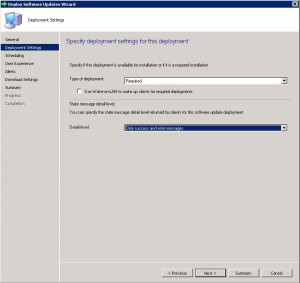
- On the Deployment Tab, leave the type of deployment as Required and choose the level of detail you want then click on Next.

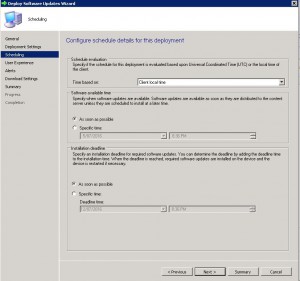
- Now to schedule when you want the update to deploy. As this is a Zero Day Exploit that you want patched quickly, schedule the patch to be available As Soon As Possible for both the Software Available Time and Installation Deadline. Please note, that more often than not, the installation of an update will cause systems to restart. Please make sure you have informed the appropriate people and that you have approval for deployment. Nothing worse than deploying an update and having to answer to Management as you caused unwarranted system outages.

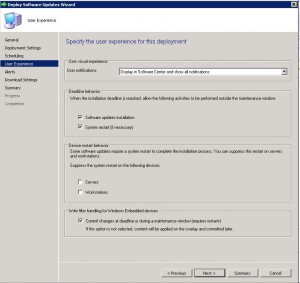
- The User Experience Tab is where you set how the deployment will interact with Users. You can set if the users are notified within the Software Centre that an update is available for installation, when the deployment deadline is reached whether the update can install and restart the system outside a maintenance window, and finally whether you wish to suppress a system restart. As this is an urgent deployment, I have chosen to allow installation and restart to be allowed outside any maintenance windows. Choose the settings you require and click on Next.

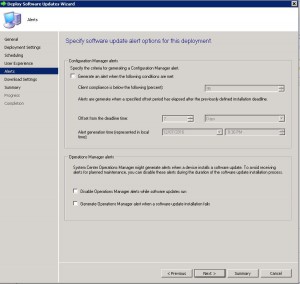
- If you have System Centre Operations Manager (Microsoft SCOM) in your environment you can choose to generate an alert with criteria you specify. In this example we are not going to specify any settings. Click on Next when you have made your selections.

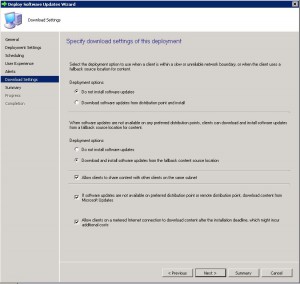
- The Download Settings tab allows you to choose client download settings. If a client is on a slow or unreliable network boundary you can choose if they dont install the update or from another distribution point. Allowing clients to share content between themselves is a great feature of SCCM as it will stop other client machines downloading the same updates and possibly flooding a network link. The clients will all share the update between themselves if they are on the same subnet. Also if they cannot download the update from a SCCM distribution point, allowing them to download from Microsoft Update is available as well.
Click on Next when ready to.
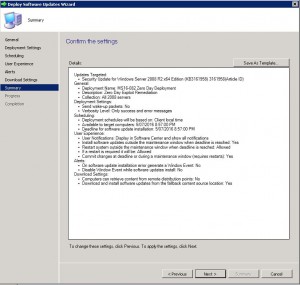
- Now you can review all the settings on the Summary Tab. Confirm you are happy with all the settings and then click Next.

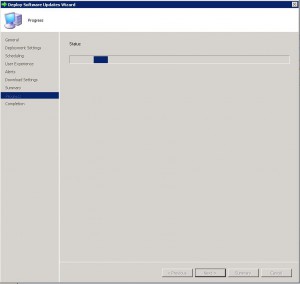
- The progress of the deployment will now be shown.

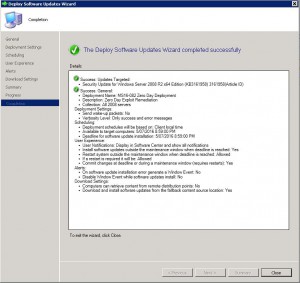
- Your Zero Day Exploit deployment should now be ready to be deployed to your SCCM clients as per the settings you have set.

Using SnaPatch for Zero Day Exploit Deployment
If you are using SnaPatch to aid you with the deployment of Windows Updates with Microsoft’s SCCM, you can follow on from Steps 1 to 4 from above.
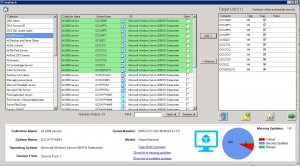
- Open the SnaPatch console and choose the SnaPatch Icon to start the snapshot and patch deployment process.

- Now you are presented with all the SCCM Collections and Systems available to deploy the Zero Day Exploit to. Choose the systems you want to receive the patch and click on Add.

If the machines are virtual (either a VMWare or HyperV virtual machine) you can choose whether to take a snapshot of the servers prior to deployment of the zero day patch. Should the servers not have a successfully snapshot completed, then they will not receive the update deployment. The snapshot of the virtual machines gives you a quick rollback position should the update cause an issue in your environment.
When you have chosen all the machines you wish and if you would like a snapshot, click on the green arrow to continue.
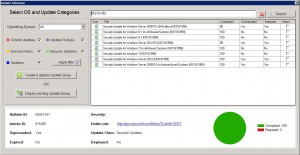
- The next window in the SnaPatch process, is to chose the update you wish to deploy. As this is a Zero Day patch and we know the Microsoft article number (which in this example is MS16-082), type in the KB or MS article number and choose search.
Select the update, confirm that it has been downloaded (as per step 3 above) and now choose if you want the update to deploy to an existing Update Group or to create a new one. 
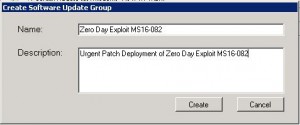
- As this is an urgent deployment, I am choosing Create & Deploy Update Group. Give the Software Update Group a Name and Description and click Create.

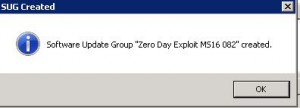
- Confirmation that the Software Update Group has been created. Click OK.

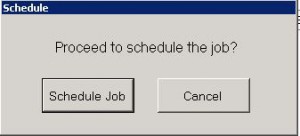
- Next we have to schedule deployment. Click Schedule Job.

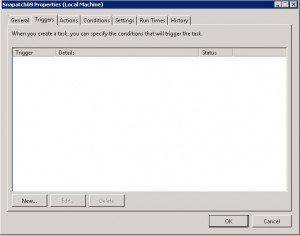
- Now on the scheduling window, click on New.

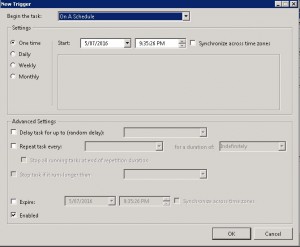
- Choose an appropriate schedule when you would like the deployment to happen. This will set up the update deployment for the time you specify. Click OK when you are ready to proceed, then close the scheduling Window.

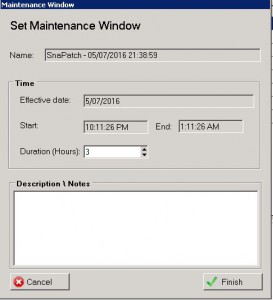
- On the Maintenance Window choose the duration you want the snapshots to be performed and the updates to be installed during. Click on Finish when complete.
 Thats all there is to it. SnaPatch will now create a deployment of the Zero Day Exploit Patch within Microsoft SCCM and set the Maintenance Window. When the maintenance window is reached, SnaPatch will interact with your Vmware or HyperV hosts and start a snapshot of the servers you have selected. Once the snapshot is complete SnaPatch then contacts SCCM and allows SCCM to deploy the patch to those servers. You will also receive email notifications throughout the snapshot and deployment process.
Thats all there is to it. SnaPatch will now create a deployment of the Zero Day Exploit Patch within Microsoft SCCM and set the Maintenance Window. When the maintenance window is reached, SnaPatch will interact with your Vmware or HyperV hosts and start a snapshot of the servers you have selected. Once the snapshot is complete SnaPatch then contacts SCCM and allows SCCM to deploy the patch to those servers. You will also receive email notifications throughout the snapshot and deployment process.
Click for further information on SnaPatch Patch Management.
Zero Day exploits can cause serious issues to programs, data, computers, and networks. It is essential to deploy patches and fixes as soon as possible to reduce the risk of exploitation. Using Microsoft SCCM 2012 to deploy a Zero Day exploit fix is an easy process that can be completed by following the steps outlined above. Keeping your hardware and software up to date and having a patching process in place are good practices to mitigate the risk of unknown vulnerabilities.











 T
T